HP 635n HP Jetdirect Print Servers - How to Use 802.1X on HP Jetdirect Print S - Page 76
EAP Unknown User Name
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 76 highlights
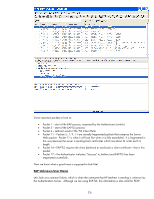
Some important packets to look at: • Packet 1 - start of the EAP process, requested by the Authenticator (switch). • Packet 3 - start of the EAP-TLS process • Packet 4 - Jetdirect sends it SSL/TLS Client Hello • Packet 11 - Packets 5, 7, 9, 11 are actually fragmented packets that comprise the Server Hello packet. Packet 11 is what it will look like when it is fully assembled. It is fragmented in this way because the server is sending back certificates which are about 3k octets each in length. • Packet 14 - EAP-TLS requires the client (Jetdirect) to send back a client certificate - that is this packet. • Packet 17 - the Authenticator indicates "Success" to Jetdirect and EAP-TLS has been negotiated successfully. Now we know what a good trace is supposed to look like! EAP Unknown User Name Let's look at a common failure, which is when the username that HP Jetdirect is sending is unknown by the Authentication Server. Although we are using EAP-TLS, this information is also valid for PEAP. 76