TP-Link TL-SL5428E User Guide - Page 11
Introduction
 |
UPC - 845973020873
View all TP-Link TL-SL5428E manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 11 highlights
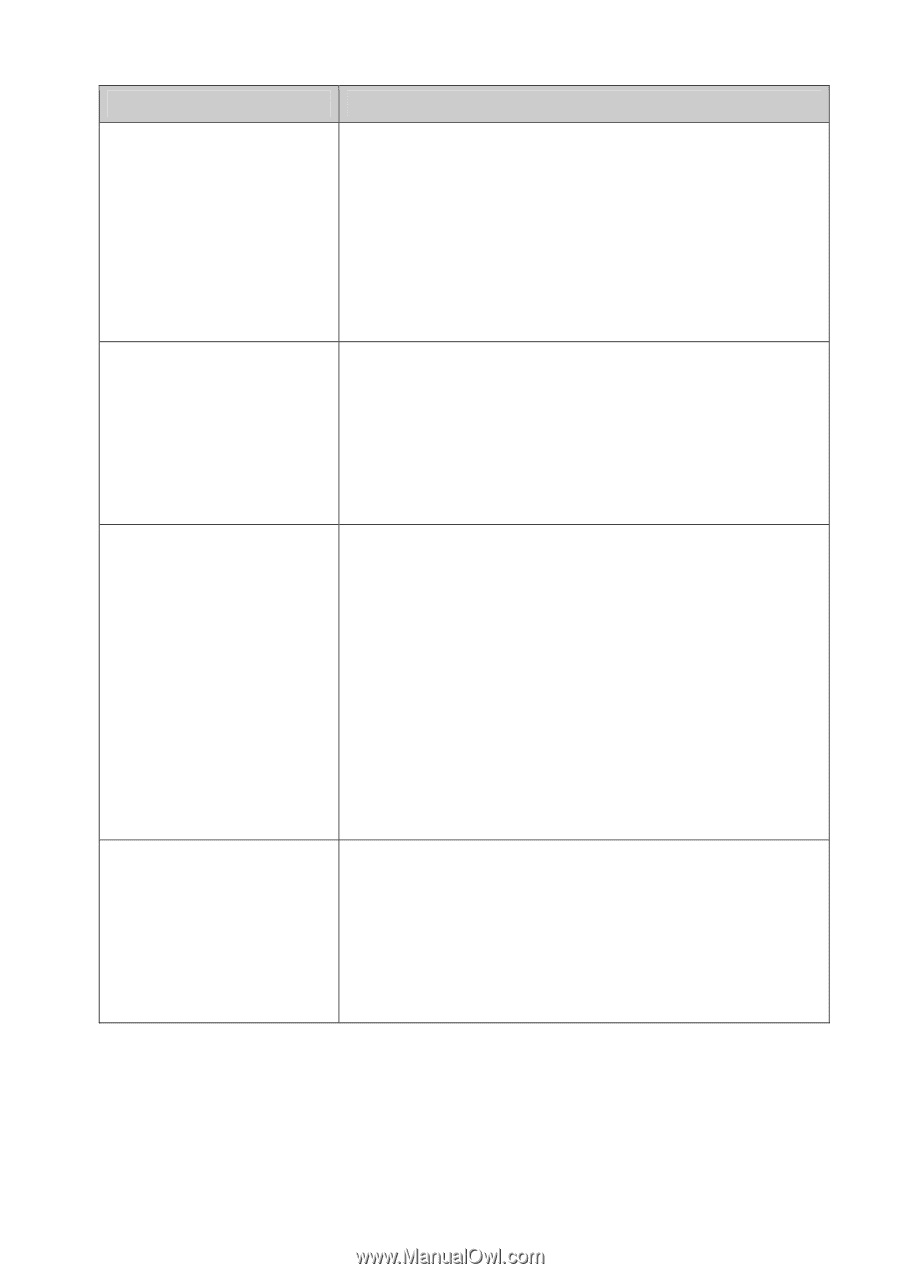
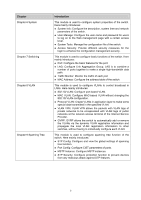
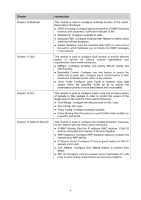
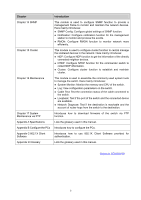
Chapter Chapter 6 System Chapter 7 Switching Chapter 8 VLAN Chapter 9 Spanning Tree Introduction This module is used to configure system properties of the switch. Here mainly introduces: z System Info: Configure the description, system time and network parameters of the switch. z User Manage: Configure the user name and password for users to log on to the Web management page with a certain access level. z System Tools: Manage the configuration file of the switch. z Access Security: Provide different security measures for the login to enhance the configuration management security. This module is used to configure basic functions of the switch. Here mainly introduces: z Port: Configure the basic features for the port. z LAG: Configure Link Aggregation Group. LAG is to combine a number of ports together to make a single high-bandwidth data path. z Traffic Monitor: Monitor the traffic of each port z MAC Address: Configure the address table of the switch. This module is used to configure VLANs to control broadcast in LANs. Here mainly introduces: z 802.1Q VLAN: Configure port-based VLAN. z MAC VLAN: Configure MAC-based VLAN without changing the 802.1Q VLAN configuration. z Protocol VLAN: Create VLANs in application layer to make some special data transmitted in the specified VLAN. z VLAN VPN: VLAN VPN allows the packets with VLAN tags of private networks to be encapsulated with VLAN tags of public networks at the network access terminal of the Internet Service Provider. z GVRP: GVRP allows the switch to automatically add or remove the VLANs via the dynamic VLAN registration information and propagate the local VLAN registration information to other switches, without having to individually configure each VLAN. This module is used to configure spanning tree function of the switch. Here mainly introduces: z STP Config: Configure and view the global settings of spanning tree function. z Port Config: Configure CIST parameters of ports. z MSTP Instance: Configure MSTP instances. z STP Security: Configure protection function to prevent devices from any malicious attack against STP features. 3