TP-Link TL-SL5428E User Guide - Page 176
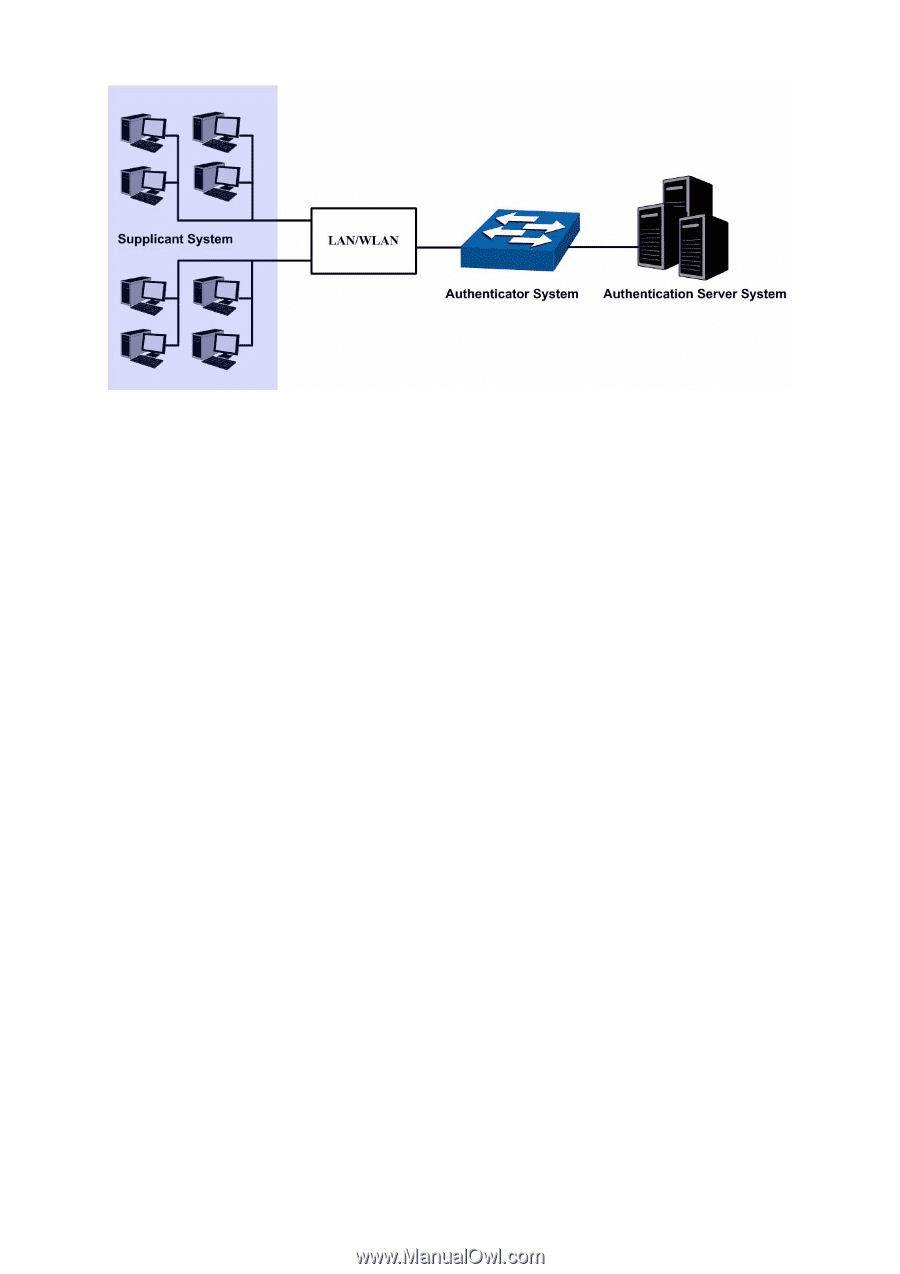
Supplicant System, Authenticator System, Authentication Server System, The Mechanism of an 802.1X
 |
UPC - 845973020873
View all TP-Link TL-SL5428E manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 176 highlights
Figure 13-19 Architecture of 802.1X authentication (1) Supplicant System: The supplicant system is an entity in LAN and is authenticated by the authenticator system. The supplicant system is usually a common user terminal computer. An 802.1X authentication is initiated when a user launches client program on the supplicant system. Note that the client program must support the 802.1X authentication protocol. (2) Authenticator System: The authenticator system is usually an 802.1X-supported network device, such as this TP-LINK switch. It provides the physical or logical port for the supplicant system to access the LAN and authenticates the supplicant system. (3) Authentication Server System: The authentication server system is an entity that provides authentication service to the authenticator system. Normally in the form of a RADIUS server. Authentication Server can store user information and serve to perform authentication and authorization. To ensure a stable authentication system, an alternate authentication server can be specified. If the main authentication server is in trouble, the alternate authentication server can substitute it to provide normal authentication service. ¾ The Mechanism of an 802.1X Authentication System IEEE 802.1X authentication system uses EAP (Extensible Authentication Protocol) to exchange information between the supplicant system and the authentication server. (1) EAP protocol packets transmitted between the supplicant system and the authenticator system are encapsulated as EAPOL packets. (2) EAP protocol packets transmitted between the authenticator system and the RADIUS server can either be encapsulated as EAPOR (EAP over RADIUS) packets or be terminated at authenticator system and the authenticator system then communicate with RADIUS servers through PAP (Password Authentication Protocol) or CHAP (Challenge Handshake Authentication Protocol) protocol packets. (3) When a supplicant system passes the authentication, the authentication server passes the information about the supplicant system to the authenticator system. The authenticator system in turn determines the state (authorized or unauthorized) of the controlled port according to the instructions (accept or reject) received from the RADIUS server. ¾ 802.1X Authentication Procedure An 802.1X authentication can be initiated by supplicant system or authenticator system. When the authenticator system detects an unauthenticated supplicant in LAN, it will initiate the 802.1X 168