ZyXEL SBG3300-N Series User Guide - Page 186
Table 77, Label, Description
 |
View all ZyXEL SBG3300-N Series manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 186 highlights
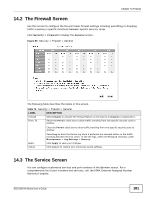
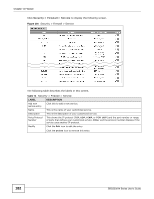
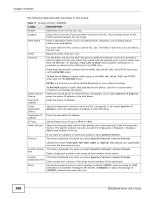
Chapter 14 Firewall The following table describes the labels in this screen. Table 77 Access Control: Add/Edit LABEL Enable Logging Filter Name DESCRIPTION Select this to turn on the ACL rule. Select this to have the Device log when it performs the ACL rule's selected action on the traffic traveling between the two zones. Enter a descriptive name of up to 16 alphanumeric characters, not including spaces, underscores, and dashes. Order Direction You must enter the filter name to add an ACL rule. This field is read-only if you are editing the ACL rule. Select the order of the ACL rule. Use the From and To drop-down list boxes to select the direction of travel of packets to which to apply this ACL rule. Select from which zone the packets come in and to which zone they are destined. For example, From LAN To WAN means packets traveling from a computer or subnet on the LAN zone to the WAN zone. From Any means traffic coming from the WAN, LAN, WLAN, DMZ, and EXTRA zones (but not the ROUTER zone). To Any (excl. Router) means traffic going to the WAN, LAN, WLAN, DMZ, and EXTRA zones (but not the ROUTER zone). EXTRA is a local zone to use as needed depending on your network topology. Select Source Device Source IP address Select Destination Device Destination IP address IP Type Select Service To ROUTER applies to traffic that destined for the Device. Use this to control which computers can manage the Device. Select the source device to which the ACL rule applies. If you select Specific IP Address, enter the source IP address in the field below. Enter the source IP address. Select the destination device to which the ACL rule applies. If you select Specific IP Address, enter the destiniation IP address in the field below. Enter the destination IP address. Select whether your IP type is IPv4 or IPv6. Select the transport layer protocol that defines your customized port from the drop-down list box. The specific protocol rule sets you add in the Security > Firewall > Service > Add screen display in this list. Protocol If you want to configure a customized protocol, select Specific Service. This field is displayed only when you select Specific Protocol in Select Protocol. Choose the IP port (TCP/UDP, TCP, UDP, ICMP, or ICMPv6) that defines your customized port from the drop-down list box. Custom Source This field is displayed only when you select Specific Protocol in Select Protocol. Port Enter a single port number or the range of port numbers of the source. Custom This field is displayed only when you select Specific Protocol in Select Protocol. Destination Port Enter a single port number or the range of port numbers of the destination. Policy Use the drop-down list box to select whether to discard (DROP), deny and send an ICMP destination-unreachable message to the sender of (REJECT) or allow the passage of (ACCEPT) packets that match this rule. 186 SBG3300-N Series User's Guide