Cisco WS-C2980G-A Software Guide - Page 381
Security Subsystem, Access Control Subsystem, Applications, Catalyst 4500 Series, Catalyst 2948G
 |
UPC - 746320423555
View all Cisco WS-C2980G-A manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 381 highlights
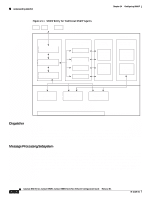
Chapter 24 Configuring SNMP Understanding SNMPv3 Security Subsystem The Security Subsystem authenticates and encrypts messages. Each outgoing message is passed to the Security Subsystem from the Message Processing Subsystem. Depending on the services required, the Security Subsystem may encrypt the enclosed PDU and some fields in the message header. In addition, the Security Subsystem may generate an authentication code and insert it into the message header. After encryption, the message is returned to the Message Processing Subsystem. Each incoming message is passed to the Security Subsystem from the Message Processing Subsystem. If required, the Security Subsystem checks the authentication code and performs decryption. The processed message is returned to the Message Processing Subsystem. An implementation of the Security Subsystem may support one or more distinct security models. So far, the only defined security model is the User-Based Security Model (USM) for SNMPv3, that is specified in RFC 2274. The USM protects SNMPv3 messages from the following potential security threats: • An authorized user sending a message that gets modified in transit by an unauthorized SNMP entity • An unauthorized user trying to masquerade as an authorized user • Anyone modifying the message stream • Anyone eavesdropping The USM currently defines the use of HMAC-MD5-96 and HMAC-SHA-96 as the possible authentication protocols and CBC-DES as the privacy protocol. SNMPv1 and SNMPv2c security models provide only weak authentication (community names) and no privacy. Access Control Subsystem The responsibility of the Access Control Subsystem is straightforward. It determines whether access to a managed object should be allowed. Currently, one access control model, the View-Based Access Control Model (VACM), has been defined. With VACM, you can control which users and which operations can have access to which managed objects. Applications SNMPv3 applications refer to internal applications within an SNMP entity. These internal applications can generate SNMP messages, respond to received SNMP messages, generate notifications, receive notifications, and forward messages between SNMP entities. Currently, there are five types of applications: • Command generators-Generate SNMP commands to collect or set management data. • Command responders-Provide access to management data. For example, processing get, get-next, get-bulk, and set pdus are used in a command responder application. • Notification originators-Initiate Trap or Inform messages. • Notification receivers-Receive and process Trap or Inform messages. • Proxy forwarders-Forward messages between SNMP entities. 78-15486-01 Catalyst 4500 Series, Catalyst 2948G, Catalyst 2980G Switches Software Configuration Guide-Release 8.1 24-13