HP 6125G HP 6125G & 6125G/XG Blade Switches ACL and QoS Configuration - Page 8
Match order, Sorts ACL rules in ascending order of rule ID. A rule with a lower ID is matched before
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 8 highlights
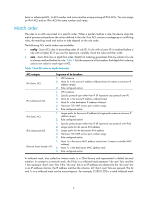
basic or advanced ACL, its ACL number and name must be unique among all IPv6 ACLs. You can assign an IPv4 ACL and an IPv6 ACL the same number and name. Match order The rules in an ACL are sorted in a specific order. When a packet matches a rule, the device stops the match process and performs the action defined in the rule. If an ACL contains overlapping or conflicting rules, the matching result and action to take depend on the rule order. The following ACL match orders are available: • config-Sorts ACL rules in ascending order of rule ID. A rule with a lower ID is matched before a rule with a higher ID. If you use this approach, carefully check the rules and their order. • auto-Sorts ACL rules in depth-first order. Depth-first ordering guarantees that any subset of a rule is always matched before the rule. Table 1 lists the sequence of tie breakers that depth-first ordering uses to sort rules for each type of ACL. Table 1 Sort ACL rules in depth-first order ACL category IPv4 basic ACL IPv4 advanced ACL IPv6 basic ACL IPv6 advanced ACL Ethernet frame header ACL Sequence of tie breakers 1. VPN instance 2. More 0s in the source IP address wildcard (more 0s means a narrower IP address range) 3. Rule configured earlier 1. VPN instance 2. Specific protocol type rather than IP (IP represents any protocol over IP) 3. More 0s in the source IP address wildcard mask 4. More 0s in the destination IP address wildcard 5. Narrower TCP/UDP service port number range 6. Rule configured earlier 1. Longer prefix for the source IP address (a longer prefix means a narrower IP address range) 2. Rule configured earlier 1. Specific protocol type rather than IP (IP represents any protocol over IPv6) 2. Longer prefix for the source IPv6 address 3. Longer prefix for the destination IPv6 address 4. Narrower TCP/UDP service port number range 5. Rule configured earlier 1. More 1s in the source MAC address mask (more 1s means a smaller MAC address) 2. More 1s in the destination MAC address mask 3. Rule configured earlier A wildcard mask, also called an inverse mask, is a 32-bit binary and represented in dotted decimal notation. In contrast to a network mask, the 0 bits in a wildcard mask represent "do care" bits, and the 1 bits represent "don't care" bits. If the "do care" bits in an IP address are identical to the "do care" bits in an IP address criterion, the IP address matches the criterion. All "don't care" bits are ignored. The 0s and 1s in a wildcard mask can be noncontiguous. For example, 0.255.0.255 is a valid wildcard mask 2