HP Integrity rx2800 Smart Setup Scripting Toolkit Administrator's Guide 4.0 - Page 10
SSTK boot image, SSTK repository, The deployment process
 |
View all HP Integrity rx2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 10 highlights
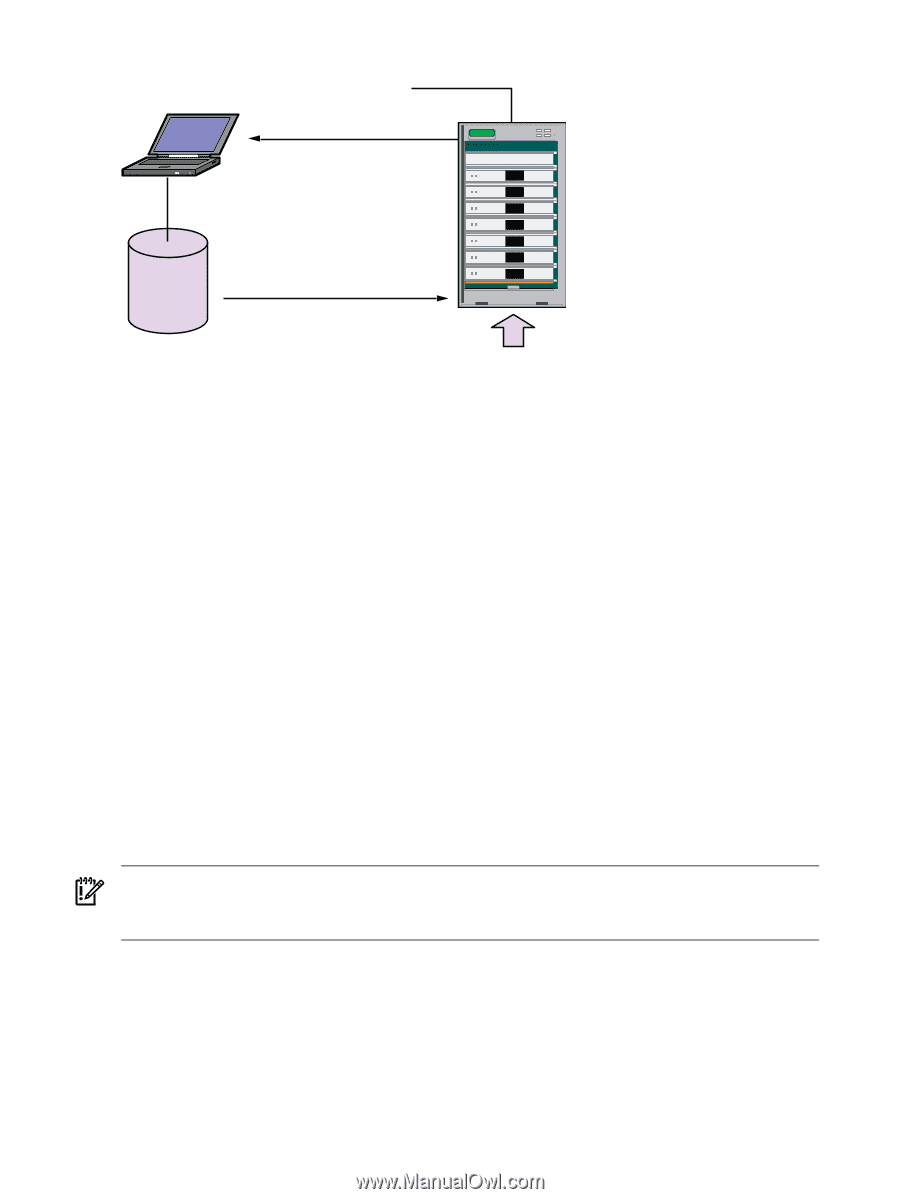
Figure 1-1 Simple SSTK Deployment Scenario CommandPrompt ReadHWConf ApplyHWConf, ApplySASConf and Deploy SSTK repository (Workstation) SSTK boot image (Target Server) You use a workstation to unpack the toolkit, edit the configuration files, and set up the boot mechanism. The workstation typically hosts the SSTK repository, which holds the configuration files, scripts, utilities, and Windows installation files. Each time the target server loads the SSTK boot image, the repository is shared and the SSTK performs a preconfigured action. Sample actions include saving the server configuration (ReadHWConf), replicating a saved configuration (ApplyHWConf), applying RAID1 configuration to a LSI SAS 1068 Controller ApplySASConf, and installing Windows (Deploy), or showing a command prompt in order to run the SSTK utilities manually (CommandPrompt). SSTK boot image The SSTK boot image is based on the Windows Pre-installation Environment (Windows PE). Windows PE is a subset of the Windows 2008 Kernel and provides operating system features for the toolkit. For more information, see the Windows PE User's Guide in the Windows Automated Installation Kit (AIK). The SSTK provides a script to create a customized boot image using AIK tools. This is described in Chapter 2 (page 15). SSTK repository Every server that boots to the SSTK environment must have access to the repository of configuration files, scripts, utilities, OS files, driver files, and application files. If you host the repository on the workstation, it must be accessible to the Integrity servers being deployed. IMPORTANT: A repository solution is not limited to the previous example. You can host the repository on a boot device (a local disk on the Integrity server or a USB device). The repository must have write permission in order to save SSTK log and data files. The deployment process The deployment process consists of the following steps: 1. Extract the SSTK software package. 2. Create an SSTK boot image. 3. Configure an SSTK action. 4. Boot the target server and monitor the deployment using the SSTK log system or Integrated Lights-Out (iLO) interface. 10 Overview