HP t420 Administrator Guide 8 - Page 62
Local Accounts, Encryption, Options,
 |
View all HP t420 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 62 highlights
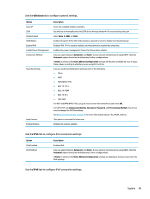
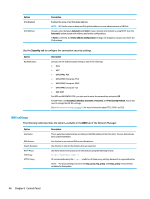
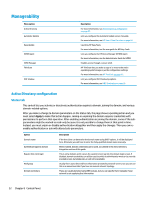
● Local Accounts on page 50 ● Encryption on page 50 ● Options on page 50 Local Accounts The Local Accounts tab can be used to change the local root and user account passwords or to disable authentication using those accounts. CAUTION: Disabling the root and/or user accounts might leave your system in an unusable state unless Active Directory authentication is enabled. For example, if the root account is disabled, you will only be able to change to administrator mode using domain credentials of an administrator. However, disabling the local accounts might improve security when Active Directory authentication is enabled because you no longer have to maintain and update a shared secret such as the thin client's root password. If Active Directory authentication has been used and there is any cached data for domain users on the thin client, you can also delete the user's cached data from this tab. NOTE: If the user logged in using a domain account, they cannot delete their own account's data because it would leave the system in an indeterminate state. Encryption Active Directory credentials and other secrets can be hashed for functions like screen-unlock and/or encrypted and stored on the system for single sign-on. The hash algorithm for creating a password's hash can be selected from this menu. The default, scrypt, is a well-accepted key derivation function. Argon2, another key derivation function is also available, as well as conventional hashes SHA-256 and SHA-512. The advantage of a key derivation function is that it is computationally expensive to compute a rainbow table that matches plain-text passwords to precomputed hash values, whereas conventional hashes are meant to execute as fast as possible. All hashes are stored with 128 or more bits of random salt which changes each time the password hash is computed and stored. Encrypted passwords are used in situations where they can be reversed and supplied to connections when they start (single sign-on). The encryption algorithm can be selected here from a wide variety supported by OpenSSL. Unless there is a good reason to select a different value, HP recommends using the default encryption algorithm, which is generally regarded as a modern, secure algorithm by the security community. The number of salt bits and key bits will vary from one algorithm to another and you can get details by pressing the info button next to the algorithm selector. Encryption keys are unique per thin client and are stored in a place that only administrators can read. Furthermore, only certain authorized applications on the system can do decryption. Both hashes and encrypted secrets can be set with a time-to-live. If the amount of time between when the secret was hashed or encrypted and the time when it is used or decrypted exceeds the time-to-live, the hashmatch or decryption will fail. By default, the single sign-on password is usable for only one day, but any passwords stored with connection or network settings can be used indefinitely. Options Local user must log in: If this option is selected when Active Directory authentication is disabled, the login screen still appears at startup and logout. In this situation, the local user or root credentials must be used to gain access to the system. Enable secret peek: If enabled, most password and secret entry fields on the system display a small eyeball icon on the right side. When that eyeball icon is selected by pressing and holding down the left mouse button, 50 Chapter 8 Control Panel