Hitachi HDS728080PLAT20 Specifications - Page 128
DEVICE CONFIGURATION IDENTIFY subcommand C2h, DEVICE CONFIGURATION SET subcommand C3h
 |
UPC - 829686000094
View all Hitachi HDS728080PLAT20 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 128 highlights
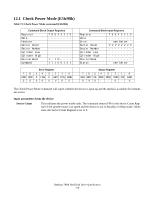
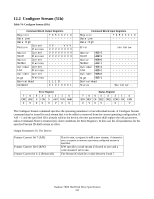
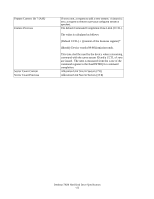
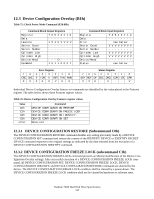
12.3.3 DEVICE CONFIGURATION IDENTIFY (subcommand C2h) The DEVICE CONFIGURATION IDENTIFY command returns a 512 byte data structure via PIO data-in transfer. The content of this data structure indicates the selectable commands, modes, and feature sets that the device is capable of supporting. If a DEVICE CONFIGURATION SET command has been issued reducing the capabilities, the response to an IDENTIFY DEVICE or IDENTIFY PACKET DEVICE command will reflect the reduced set of capabilities, while the DEVICE CONFIGURATION IDENTIFY command will reflect the entire set of selectable capabilities. The format of the Device Configuration Overlay data structure is shown in Table 77: "Device Configuration Overlay Data structure" on page 125. 12.3.4 DEVICE CONFIGURATION SET (subcommand C3h) The DEVICE CONFIGURATION SET command allows a device manufacturer or a personal computer system manufacturer to reduce the set of optional commands, modes, or feature sets supported by a device as indicated by a DEVICE CONFIGURATION IDENTIFY command. The DEVICE CONFIGURATION SET command transfers an overlay that modifies some of the bits set in words 63, 82, 83, 84, and 88 of the IDENTIFY DEVICE command response. When the bits in these words are cleared, the device no longer support the indicated command, mode, or feature set. If a bit is set in the overlay transmitted by the device that is not set in the overlay received from a DEVICE CONFIGURATION IDENTIFY command, no action is taken for that bit. The format of the overlay transmitted by the device is described in the table in Table 77: "Device Configuration Overlay Data structure" on page 125. The restrictions on changing these bits is described in the text following that table. If any of the bit modification restrictions described are violated or any setting is changed with DEVICE CONFIGURATION SET command, the device shall return command aborted. At that case, error reason code is returned to sector count register, invalid word location is returned to cylinder high register, and invalid bit location is returned to cylinder low register. The Definition of error information is shown in Table 78: "DCO error information definition" on page 126. ERROR INFORMATION EXAMPLE 1: If a user attempts to change maximum LBA address (DC SET or DC RESTORE) after establishing a protected area with SET MAX address, the device will abort that command and returns error reason code as below. Cylinder high Cylinder low Sector Number Sector count : 03h : 00h : 00h : 06h = word 3 is invalid this register is not assigned in this case this register is not assigned in this case = Protected area is now established ERROR INFORMATION EXAMPLE 2: If the user attempts to disable that feature when the device is enabled and the Security feature is set, the device will abort that command and returns an error reason code as below. Cylinder high Cylinder low Sector Number Sector count : 07h : 08h : 08h : 04h = word 7 is invalid = bit 3 is invalid = bit 3 is invalid = Security feature set is now enabled Deskstar 7K80 Hard Disk Drive Specification 124