Konica Minolta C250i bizhub C360i/C300i/C250i Security Operations User Manual - Page 35
Setting IPsec
 |
View all Konica Minolta C250i manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 35 highlights
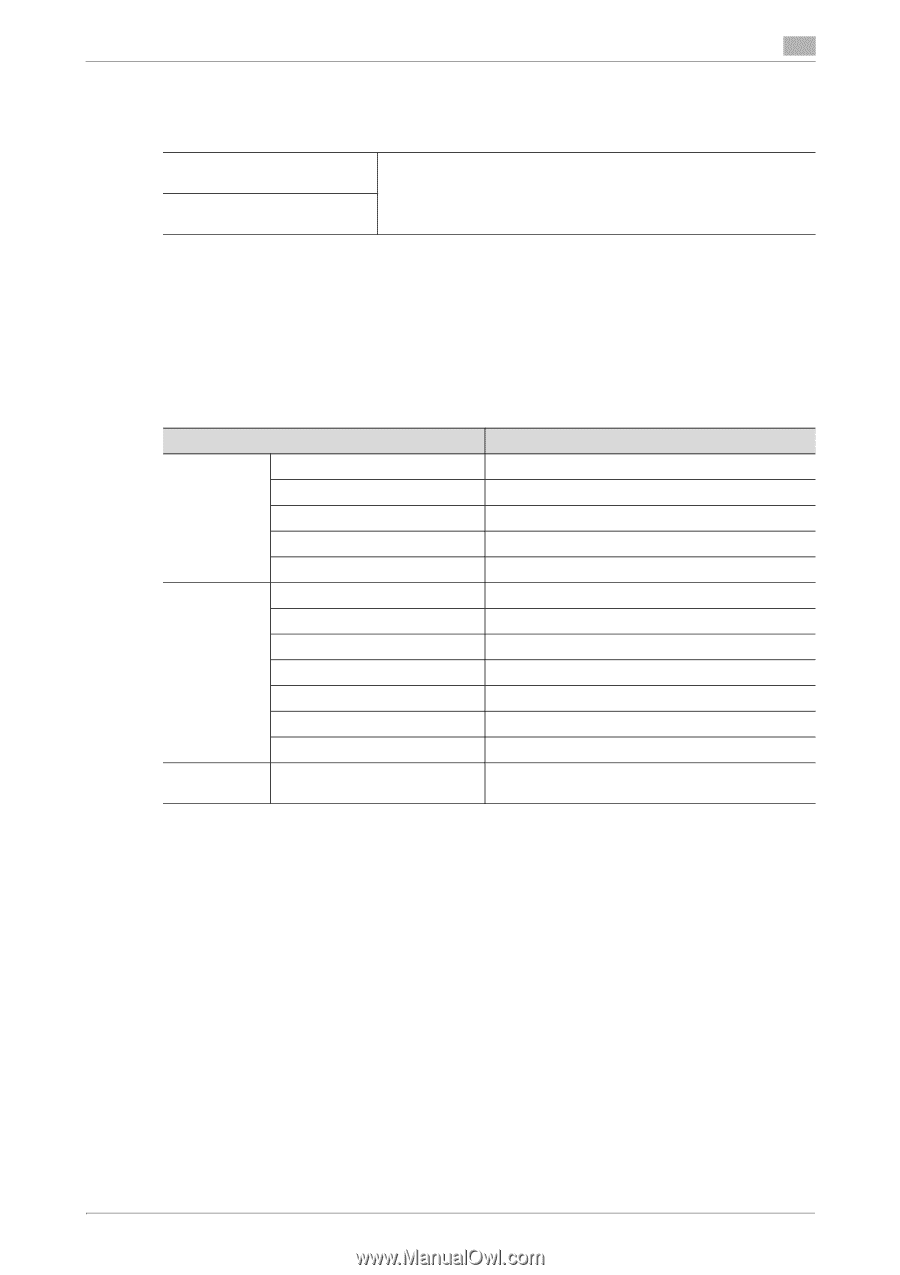
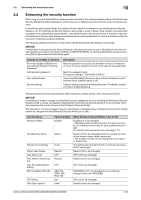
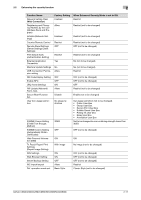
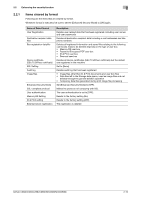
2.4 Setting IPsec 2 2.4 Setting IPsec The following are the authentication algorithms for the IPsec communication. IPsec IKE authentication algorithm IPsec ESP authentication algorithm • SHA-1 • SHA-2 (256bit/384bit/512bit) 2.4.1 IPsec setting The Web connection needs to be used to set the device certificate and an external certificate used in the IPsec network setting. Refer to "Home > Web Management Tool > Reinforcing Security > Encrypting Communications > Using IPsec communication" in the HTML manual for registration before setting [Enhanced Security Mode] to [ON]. Any certificate other than the IPsec certificate cannot be registered. Use [IPsec Setting] in the settings below. Setting item IKEv1 SA Peer [Encryption Algorithm] [Authentication Algorithm] [Encryption Key Validity Period] [Diffie-Hellman Group] [Negotiation Mode] [Encapsulation Mode] [Security Protocol] [Key Exchange Method] [Lifetime After Establishing SA] [Authentication Method] [ESP Encryption Algorithm] [ESP Authentication Algorithm] [Pre-Shared Key Text] Setting value AES-CBC (128bit/256bit) SHA-1 or SHA-2 (256bit/384bit/512bit) 600 to 86,400 sec. (set within 24 hours) Group 14 Main Mode (default) Transport (default) ESP IKEv1 (default) 600 to 28,800 sec. (set within 8 hours) Pre-Shared Key or Digital Signature AES-CBC (128bit/256bit) SHA-1 or SHA-2 (256bit/384bit/512bit) ASCII code (2 to 128 characters) or HEX code (up to 256 characters) When using [Pre-Shared Key] in the machine for the authentication method of the communication counterpart, set a hard-to-guess value to [Pre-Shared Key Text] to prevent the value from leaking to nobody but the counterpart, in an appropriate manner. Do not set a value that can be easily guessed such as a birthday and an employee identification number. It is recommended, from the viewpoint of security, to set a large-size key of 128 characters or less. Leakage of the Pre-Shared Key strings of IPsec that have been set to the MFP results in an increased risk of spoofing of the MFP. Set different Pre-Shared Key strings for each device and safely keep them. Set and use strings that cannot be deciphered by dictionary attack and brute force attack, without using words in a dictionary and/or easily guessable strings. [SHA-1] of [IPsec Setting] - [IKEv-1] - [Authentication Algorithm] and [Digital Signature] of [IPsec Setting] [SA] - [IKE Setting] - [Authentication Method] cannot be set simultaneously. The setting set earlier is given priority. A certificate for the machine that has been issued by the reliable CA (certification authority) is required to adopt [Digital Signature Certificate] for the authentication method. To verify the chain of a presented certificate, the certificate for the CA issuing the presented certificate needs to be imported. For details of the procedure, see page 2-67. The administrator should regularly check the certificate for devices in communication with the machine by using the digital signature certificate. When finding that the certificate is invalid (expired), the administrator must immediately cease the communication with the relevant device. To resume the communication with the bizhub C360i/C300i/C250i/C036DNi/C030DNi/C025DNi 2-15