TP-Link Auranet EAP120 EAP Controller Software V2 User Guide - Page 24
Insight Tab
 |
View all TP-Link Auranet EAP120 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 24 highlights
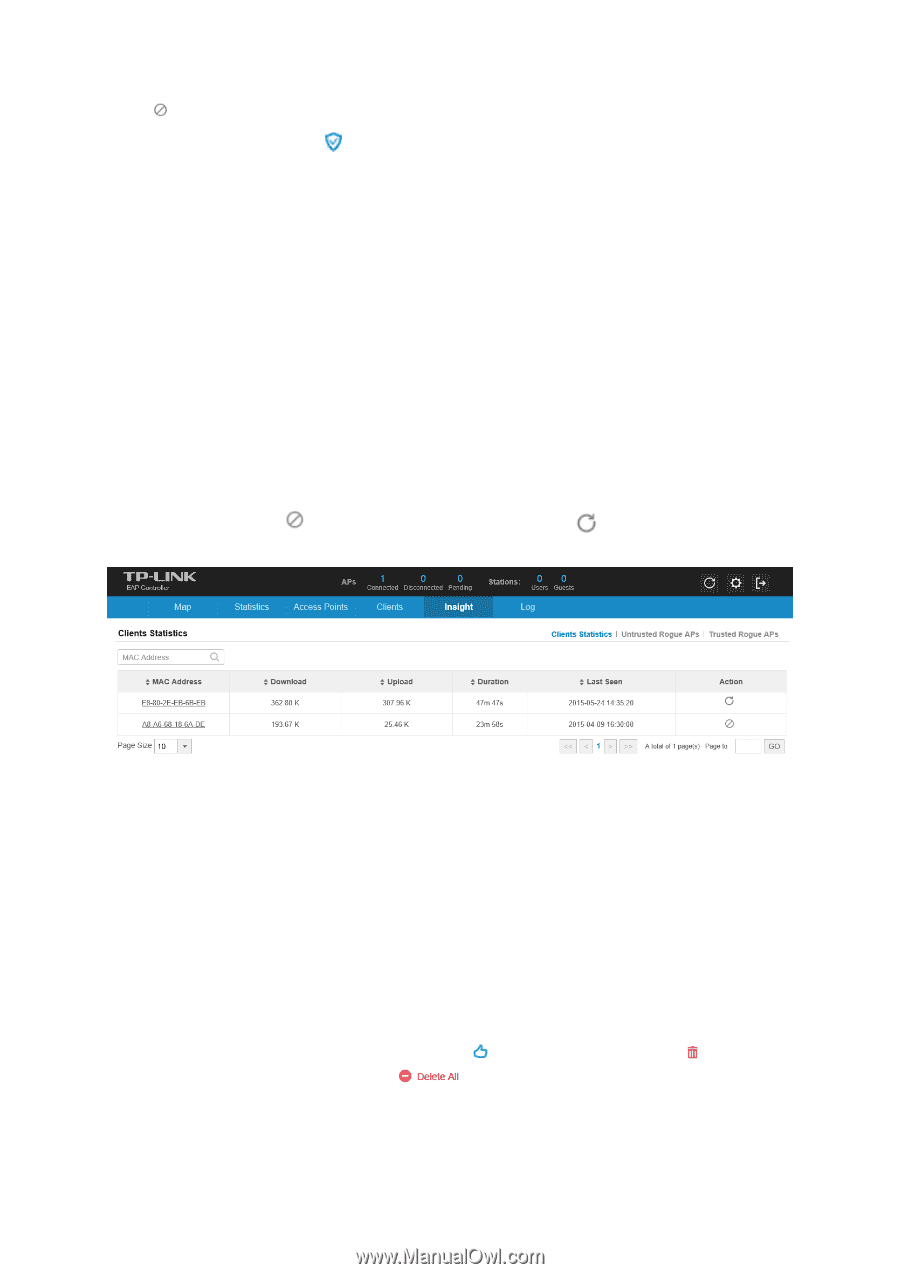
Click to restrict the client's access to the network. If the client is Guest, you can click in the Action column to cancel the authorization for it. In the MAC Address column, click the MAC address to get the client's connection history. This connection history window displays the connection date/time, duration and the client's download/upload bytes. 3.5 Insight Tab The Insight tab displays a list of clients that have connected to the EAPs network during the specified period. Clients Statistics tab and Untrusted/Trusted Rogue APs tab will be introduced separately. 3.5.1 Clients Statistics All the previously connected clients and their MAC address, download/upload bytes, duration and the time of last seen will be displayed in the Clients Statistics page. You can click the MAC address to get its connection history. Click to restrict the client's access, and click to resume the client's access. 3.5.2 Untrusted Rogue APs A Rogue AP is an access point that has been installed on a secure network without explicit authorization from a system administrator. The EAP Controller can scan all channels to detect all APs in the vicinity of the network. During the detection, clients will disconnect with EAPs. If rogue APs are detected, they will be shown on the Untrusted Rogue APs list. The Untrusted Rogue APs page displays the untrusted rogue APs' MAC address, SSID, band, channel, security mode, total number of Beacon, signal strength and the time of last seen. If you want to move an untrusted rogue AP to the Trusted Rogue AP list, click in the Action column. Click in the Action column to delete the specified record. Click to delete all the records. 20