TP-Link T1500G-8T T1500G-10PSUN V1 User Guide - Page 192
Application Authentication List Config
 |
View all TP-Link T1500G-8T manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 192 highlights
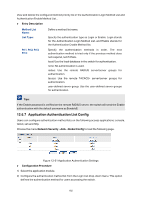
View and delete the configured method priority list in the Authentication Login Method List and Authentication Enable Method List. . Entry Description Method List Name: List Type: Pri1, Pri2, Pri3, Pri4: Define a method list name. Specify the authentication type as Login or Enable. Login stands for the Authentication Login Method List, and Enable stands for the Authentication Enable Method list. Specify the authentication methods in order. The next authentication method is tried only if the previous method does not respond, not if it fails. local: Use the local database in the switch for authentication. none: No authentication is used. radius: Use the remote RADIUS server/server groups for authentication. tacacs: Use the remote TACACS+ server/server groups for authentication. user-defined server group: Use the user-defined server groups for authentication. Tips: If the Enable password is verified on the remote RADIUS server, the switch will send the Enable authentication with the default username as $enable$. 12.6.7 Application Authentication List Config Users can configure authentication method lists on the following access applications: console, telnet, ssh and http. Choose the menu Network Security→AAA→Global Config to load the following page. Figure 12-31 Application Authentication Settings Configuration Procedure 1) Select the application module. 2) Configure the authentication method list from the Login List drop-down menu. This option defines the authentication method for users accessing the switch. 182