TP-Link T1500G-8T T1500G-10PSUN V1 User Guide - Page 38
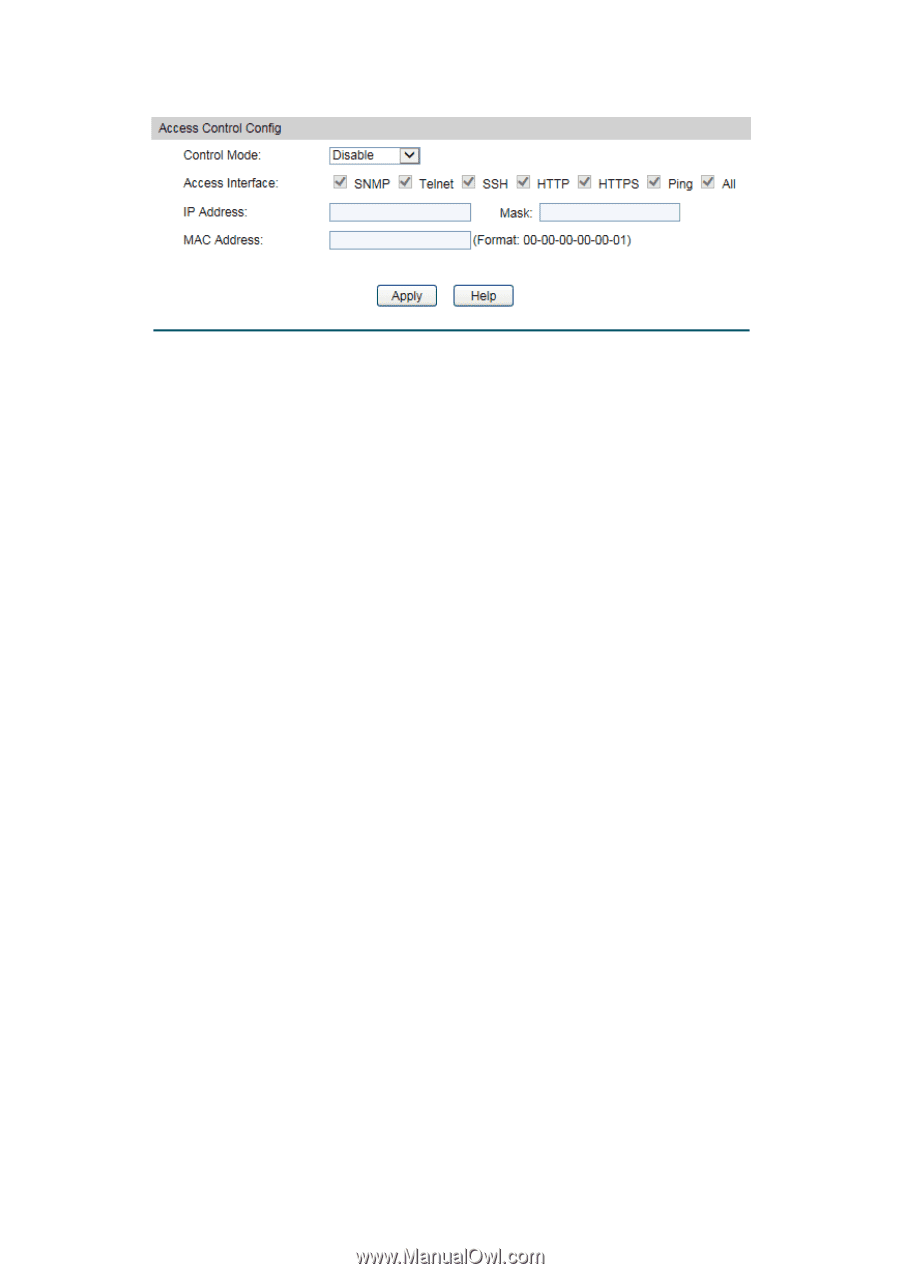
System, Access Security, Access Control, Access Control Config
 |
View all TP-Link T1500G-8T manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
Choose the menu System→Access Security→Access Control to load the following page. Figure 4-16 Access Control The following entries are displayed on this screen: Access Control Config Control Mode: Access Interface: Select the control mode for users to log on to the Web management page. Disable: Select to disable Access Control function. IP-based: Select this option to limit the IP-range of the users for login. MAC-based: Select this option to limit the MAC Address of the users for login. Port-based: Select this option to limit the ports for login. Select the interface for access control to apply. IP Address & Mask These fields is available to configure only when IP-based mode is selected. Only the users within the IP-range you set here are allowed for login. MAC Address: The field is available to configure only when MAC-based mode is selected. Only the user with this MAC Address you set here are allowed for login. 4.4.2 HTTP Config With the help of HTTP (Hyper Text Transfer Protocol), you can manage the switch through a standard browser. The standards development of HTTP was coordinated by the Internet Engineering Task Force and the World Wide Web Consortium. On this page you can configure the HTTP function. 28