TP-Link T2500-28TCTL-SL5428E T2500-28TCUN V1 User Guide - Page 240
Global Config, Authentication Method List
 |
View all TP-Link T2500-28TCTL-SL5428E manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 240 highlights
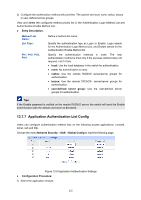
Username and password pairs are used for login and privilege authentication. The authentication can be processed locally in the switch or centrally in the RADIUS/TACACS+ server(s). The local authentication username and password pairs can be configured in 4.2 User Management. Applicable Access Application The authentication can be applied on the following access applications: Console, Telnet, SSH and HTTP. Authentication Method List A method list describes the authentication methods and their sequence to authenticate a user. The switch supports Login List for users to gain access to the switch, and Enable List for normal users to gain administrative privileges. The administrator can set the authentication methods in a preferable order in the list. The switch uses the first listed method to authenticate users, if that method fails to respond, the switch selects the next authentication method in the method list. This process continues until there is a successful communication with a listed authentication method or until all defined methods are exhausted. If authentication fails at any point in this circle, which means the secure server or the local switch denies the user's access, the authentication process stops and no other authentication methods are attempted. 802.1X Authentication 802.1X protocol uses the RADIUS to provide detailed accounting information and flexible administrative control over authentication process. The Dot1x List feature defines the RADIUS server groups in the 802.1X authentication. RADIUS/TACACS+ Server Users can configure the RADIUS/TACACS+ servers for the connection between the switch and the server. Server Group Users can define the authentication server group with up to several servers running the same secure protocols, either RADIUS or TACACS+. Users can set these servers in a preferable order, which is called the server group list. When a user tries to access the switch, the switch will ask the first server in the server group list for authentication. If no response is received, the second server will be queried, and so on. The switch has two built-in authentication server group, one for RADIUS and the other for TACACS+. These two server groups cannot be deleted, and the user-defined RADIUS/TACACS+ server will join these two server groups automatically. 13.7.1 Global Config This page is used to enable/disable the AAA function globally. Choose the menu Network Security→AAA→Global Config to load the following page. Figure 13-1 AAA Global Config Configuration Procedure: 230