TRENDnet TEW-311BRP Manual - Page 85
Inter, net/I - port forwarding
 |
View all TRENDnet TEW-311BRP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 85 highlights
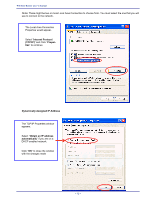
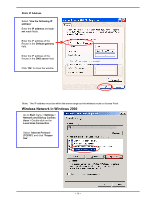
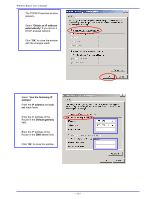
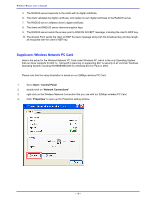
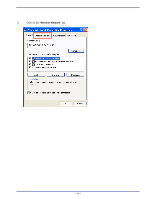
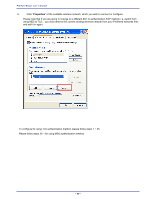
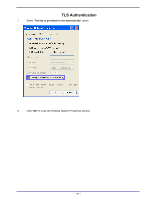
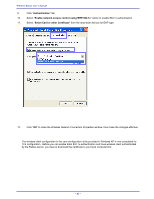
APPENDIX D: 802.1X AUTHENTICATION SETUP There are three essential components to the 802.1x infrastructure: (1) Supplicant, (2) Authenticator and (3) Server. The 802.1x security supports both MD5 and TLS Extensive Authentication Protocol (EAP). The 802.1x Authentication is a complement to the current WEP encryption used in wireless network. The current security weakness of WEP encryption is that there is no key management and no limitation for the duration of key lifetime. 802.1x Authentication offers key management, which includes key per user and key per session, and limits the lifetime of the keys to certain duration. Thus, key decryption by unauthorized attacker becomes extremely difficult, and the wireless network is safely secured. We will introduce the 802.1x Authentication infrastructure as a whole and going into details of the setup for each essential component in 802.1x authentication. 802.1x Authentication Infrastructure 802.11 Wireless Access Points Support 802.1X Authentication Request Public 802.11 Wireless Networks 802.11 Wireless Clients Support 802.1X RADIUS Server Authentication Success Inter net/I ntra- t The Infrastructure diagram showing above illustrates that a group of 802.11 wireless clients is trying to form a 802.11 wireless network with the Access Point in order to have access to the Internet/Intranet. In 802.1x authentication infrastructure, each of these wireless clients would have to be authenticated by the Radius server, which would grant the authorized client and notified the Access Point to open up a communication port to be used for the granted client. There are 2 Extensive Authentication Protocol (EAP) methods supported: (1) MD5 and (2) TLS. MD5 authentication is simply a validation of existing user account and password that is stored in the server with what are keyed in by the user. Therefore, wireless client user will be prompted for account/password validation every time when he/she is trying to get connected. TLS authentication is a more complicated authentication, which involves using certificate that is issued by the Radius server, for authentication. TLS authentication is a more secure authentication, since not only the Radius server authenticates the wireless client, but also the client can validate the Radius server by the certificate that it issues. The authentication request from wireless clients and reply by the Radius Server and Access Point process can be briefed as follows: 1. The client sends an EAP start message to the Access Point 2. The Access Point replies with an EAP Request ID message 3. The client sends its Network Access Identifier (NAI) - its user name - to the Access Point in an EAP Respond message. 4. The Access Point forwards the NAI to the RADIUS server with a RADIUS Access Request message. - 77 -