ZyXEL GS2200-8 User Guide - Page 211
DHCP Snooping Overview
 |
View all ZyXEL GS2200-8 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 211 highlights
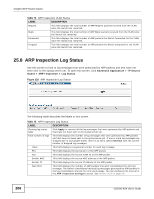
Chapter 25 IP Source Guard Table 78 ARP Inspection VLAN Configure (continued) LABEL Log DESCRIPTION Specify when the Switch generates log messages for receiving ARP packets from the VLAN. None: The Switch does not generate any log messages when it receives an ARP packet from the VLAN. Deny: The Switch generates log messages when it discards an ARP packet from the VLAN. Permit: The Switch generates log messages when it forwards an ARP packet from the VLAN. Apply Cancel All: The Switch generates log messages every time it receives an ARP packet from the VLAN. Click Apply to save your changes to the Switch's run-time memory. The Switch loses these changes if it is turned off or loses power, so use the Save link on the top navigation panel to save your changes to the non-volatile memory when you are done configuring. Click this to reset the values in this screen to their last-saved values. 25.10 Technical Reference This section provides technical background information on the topics discussed in this chapter. 25.10.1 DHCP Snooping Overview Use DHCP snooping to filter unauthorized DHCP packets on the network and to build the binding table dynamically. This can prevent clients from getting IP addresses from unauthorized DHCP servers. 25.10.1.1 Trusted vs. Untrusted Ports Every port is either a trusted port or an untrusted port for DHCP snooping. This setting is independent of the trusted/untrusted setting for ARP inspection. You can also specify the maximum number for DHCP packets that each port (trusted or untrusted) can receive each second. Trusted ports are connected to DHCP servers or other switches. The Switch discards DHCP packets from trusted ports only if the rate at which DHCP packets arrive is too high. The Switch learns dynamic bindings from trusted ports. Note: If DHCP is enabled and there are no trusted ports, DHCP requests will not succeed. Untrusted ports are connected to subscribers. The Switch discards DHCP packets from untrusted ports in the following situations: • The packet is a DHCP server packet (for example, OFFER, ACK, or NACK). • The source MAC address and source IP address in the packet do not match any of the current bindings. • The packet is a RELEASE or DECLINE packet, and the source MAC address and source port do not match any of the current bindings. • The rate at which DHCP packets arrive is too high. GS2200-8/24 User's Guide 211