ZyXEL NWA1100 User Guide - Page 20
Access Point, 1.2.2 Bridge / Repeater, Introducing the NWA, NWA1100-N User's Guide
 |
View all ZyXEL NWA1100 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 20 highlights
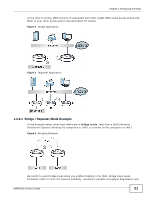
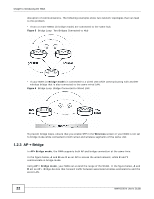
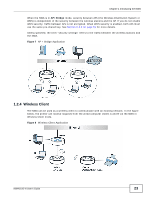
Chapter 1 Introducing the NWA 1.2.1 Access Point The NWA is an ideal access solution for wireless Internet connection. A typical Internet access application for your NWA is shown as follows. Stations A, B and C can access the wired network through the NWAs. Figure 1 Access Point Application 1.2.2 Bridge / Repeater The NWA can act as a wireless network bridge and establish wireless links with other APs. In the figure below, the two NWAs (A and B) are connected to independent wired networks and have a bridge connection (A can communicate with B) at the same time. A NWA in repeater mode (C in Figure 3) has no Ethernet connection. When the NWA is in bridge mode, you should enable Spanning Tree Protocol (STP) to prevent bridge loops. When the NWA is in Bridge / Repeater mode, security between APs (the Wireless Distribution System or WDS) is independent of the security between the wireless stations and the AP. If you do not enable WDS security, traffic between APs is not encrypted. When WDS security is enabled, both APs must use the same pre-shared key. See Section 6.4.2 on page 65 for more details. Once the security settings of peer sides match one another, the connection between devices is made. 20 NWA1100-N User's Guide