HP StorageWorks 1606 HP StorageWorks FOS 6.3.0b Release Notes (5697-0360, Apri - Page 38
Encryption behavior
 |
View all HP StorageWorks 1606 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
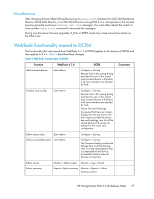
Function WebTools 6.1.0 FCIP tunnel configuration Port Admin Module > GigE tab DCFM Configure > FCIP tunnel GigE ports interface GigE ports route Non-local switch ports display in zoning tree Port Admin Module > GigE tab Configure > FCIP tunnel Port Admin Module > GigE tab Configure > FCIP tunnel Zone Admin Admin Domain Switch Admin > DCC policies Performance Monitoring Configure > Zoning Comments Viewing FCIP tunnels is still supported in WebTools 6.1.1, but New, Edit Config, and Delete are available only in DCFM. In WebTools, non-local switch port id/WWN can be added using text box. Remove Offline or inaccessible Devices Zone Admin Configure > Zoning Replace/Replace All zone members by selecting the offline devices from the zone tree. Offline devices have an unknown overlay badge with good visibility. Zone database summary Zone Admin ping Configure > Zoning Zoning report for both online and offline database Encryption behavior • HP recommends that the encrypted LUN containers be created when all of the nodes/encryption engines (EEs) in the Data Encryption Key (DEK)/High Availability Cluster (HAC) are up and enabled. • If two Encryption Engines are part of a High Availability Cluster, configure the host/target pair such that they form a multipath from both EEs. Avoid connecting both the host/target pairs to the same EE. This connectivity does not give full redundancy in case of EE failure resulting in HAC failover. • Since the quorum disk plays a vital role in keeping the cluster in sync, configure the quorum disk to be outside of the encryption environment. • LUN configuration • To configure a LUN for encryption: • Add the LUN as clear-text to the Crypto Target Container (CTC). • When the LUN comes online and the clear-text host I/O starts, modify the LUN from cleartext to encrypted, including the enable_encexistingdata option to convert the LUN from clear-text to encrypted. 38