HP StorageWorks 1606 HP StorageWorks FOS 6.3.0b Release Notes (5697-0360, Apri - Page 41
Relative to the Encryption SAN Switch and a DC SAN Director with Encryption FC blade, all nodes
 |
View all HP StorageWorks 1606 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 41 highlights
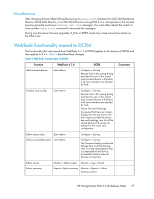
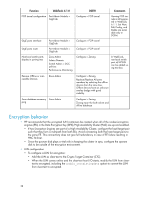
• In a DC SAN Director or DC04 SAN Director with FOS 6.3.0 and DC Switch encryption FC blades installed, you must set the quorum size to zero and disable the system card on the blade prior to downgrading to a FOS version earlier than 6.3.0. • The System Card feature requires DCFM 10.3.0 or later. Note that all nodes in the EG must be running FOS 6.3.0 for system verification to be properly supported. • The Encryption SAN Switch and Encryption FC blade do not support QoS. When using encryption or Frame Redirection, participating flows should not be included in QoS Zones. • HP encryption devices can be configured for either disk or tape operation. The ability to configure multiple Crypto-Target Containers defining different media types on a single encryption engine (Encryption SAN Switch or Encryption FC blade) is not supported. Encryption FC blades can be configured to support different media types within a common DC SAN Director/DC04 SAN Director chassis. • SKM is supported with Multiple Nodes and Dual SKM Key Vaults. Two-way certificate exchange is supported. See the Encryption Admin Guide for configuration information. If you are using dual SKMs on Encryption SAN Switch/Encryption FC blade Encryption Group, these SKM Appliances must be clustered. Failure to cluster will result in key creation failure. Otherwise, register only one SKM on the Encryption SAN Switch/Encryption FC blade Encryption Group. • When the tape key expires in the middle of write operation on the tape, the key is used to append the data on the tape media. When the backup application rewinds the media and starts writing to Block-0 again (and if the key is expired), a new key is created and used henceforth. The expired key is then marked as read only and used only for restoring data from previously encrypted tapes. • With Windows and Veritas Volume Manager/Veritas Dynamic Multipathing, when LUN sizes less than 400 MB are presented to the Encryption SAN Switch for encryption, a host panic may occur; this configuration is not supported for the FOS 6.3 release. • HCL from FOS 6.2.x to 6.3.0 is supported. Cryptographic operations and I/O will be disrupted but other layer 2 traffic will not be. • Relative to the Encryption SAN Switch and a DC SAN Director with Encryption FC blade, all nodes in the Encryption Group must be at the same firmware level of FOS 6.2 or 6.3 before starting a rekey or First Time Encryption operation. Make sure that existing rekey or First Time Encryption operations complete before upgrading any of the encryption products in the Encryption Group. Also, make sure that the upgrade of all nodes in the Encryption Group to FOS 6.3.0 completes before starting a rekey or First Time Encryption operation. • To clean up the stale rekey information for the LUN, use one of the following methods: • Method 1 1. Modify the LUN policy from encrypt to cleartext and commit. The LUN will become disabled. 2. Enable the LUN using cryptocfg --enable -LUN. Modify the LUN policy from clear-text to encrypt with enable_encexistingdata to enable the first time encryption and do commit. This will clear the stale rekey metadata on the LUN and the LUN can be used again for encryption. • Method 2 1. Remove the LUN from Crypto Target Container and commit. 2. Add the LUN back to the Crypto Target Container with LUN State="clear-text", policy="encrypt" and enable_encexistingdata set for enabling the First Time Encryption and commit. This will clear the stale rekey metadata on the LUN and the LUN can be used again for encryption. HP StorageWorks FOS 6.3.0b Release Notes 41