HP 303B Maintenance & Service Guide: HP 303B Microtower Business PC - Page 45
Computer Setup F10 Utilities, Computer Setup-Power continued
 |
View all HP 303B manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 45 highlights
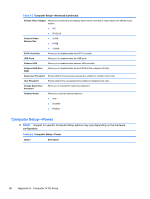
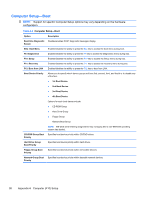
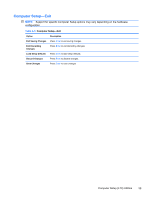
Table A-3 Computer Setup-Power (continued) After AC Power Failure Allows you to select system restart behavior after power loss: ● Stay Off ● Power On ● Auto XD Disables/enables XD (eXecute Disable) bit. NOTE: The XD bit is a technology used in to separate areas of memory for use by either storage of processor instructions or code or for storage of data. Memory designated with the NX attribute may only be used for storing data. Processor instructions should not reside and cannot be executed there. This technology is used to prevent buffer overflow attacks - malicious software that takes over computers by inserting code into another program's data storage area and running that code. Computer Setup (F10) Utilities 37

Table A-3
Computer Setup—Power (continued)
After AC Power
Failure
Allows you to select system restart behavior after power loss:
●
Stay Off
●
Power On
●
Auto
XD
Disables/enables XD (eXecute Disable) bit.
NOTE:
The XD bit is a technology used in to separate areas of memory for use by either storage
of processor instructions or code or for storage of data. Memory designated with the NX attribute
may only be used for storing data. Processor instructions should not reside and cannot be
executed there. This technology is used to prevent buffer overflow attacks – malicious software
that takes over computers by inserting code into another program's data storage area and running
that code.
Computer Setup (F10) Utilities
37