TP-Link 13dBi CPE510 V1 UG - Page 58
IP&MAC Binding, IP Range, Port Range
 |
View all TP-Link 13dBi manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 58 highlights
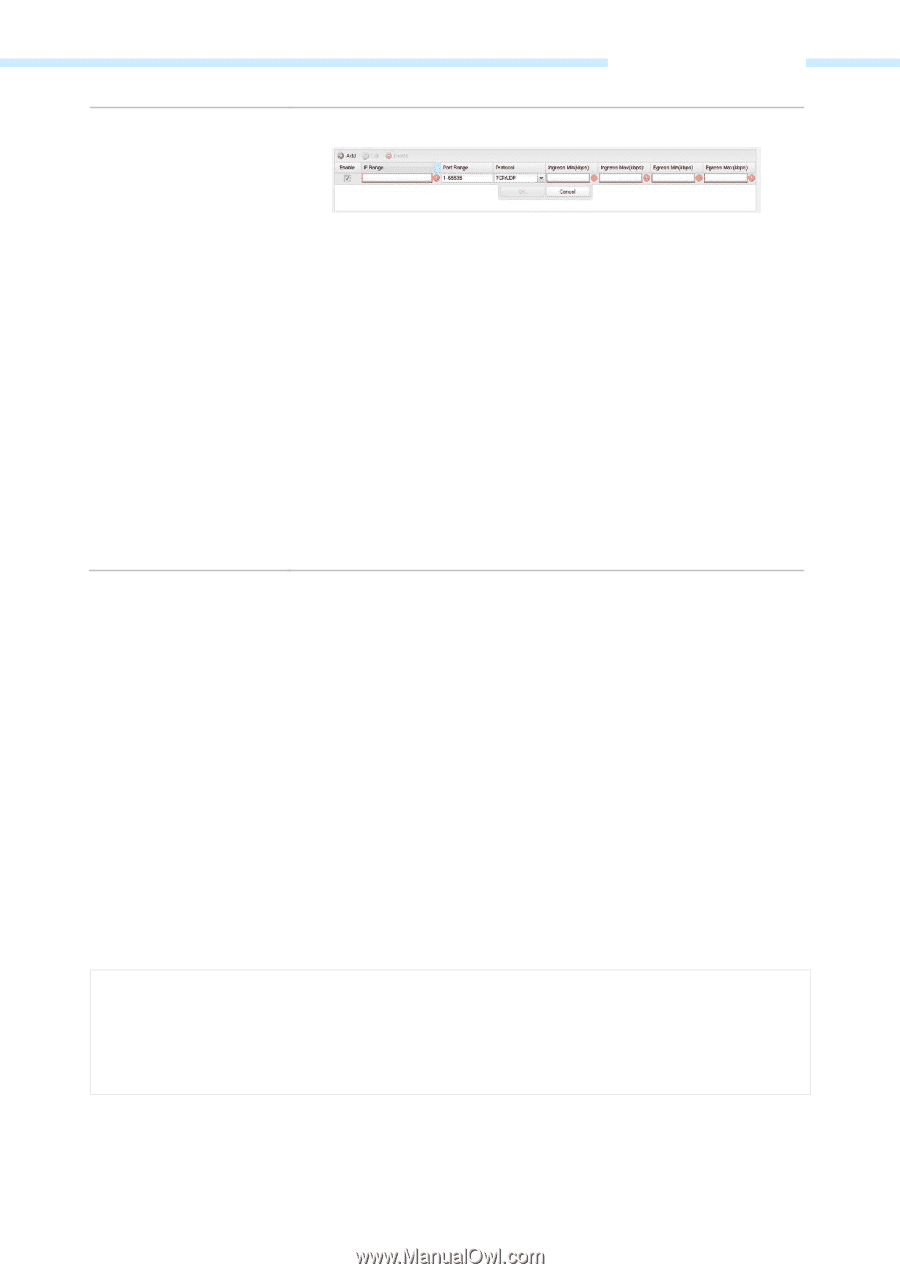
Bandwidth Control Chapter 5 Network Tab Check the Enable box to use the bandwidth control function. To use the bandwidth control: 1. Click Add in the table of bandwidth control. 2. Enter the IP Range of the target hosts which need to be controlled of bandwidth, for example 192.168.0.12-192.168.0.25. 3. Enter the Port Range through which the target hosts visit external server, for example 1-63258. 4. Choose one of the protocols used for this application: TCP, UDP, or TCP/UDP. 5. Enter the minimum ingress, maximum ingress, minimum egress and maximum egress of these IP addresses. 6. Click OK after finishing the configuration. Select the added entries, you can edit or delete them. IP&MAC Binding We can effectively prevent ARP attack and IP embezzlement by enabling the IP&MAC binding. Within the local network, the device transmits IP packets to the certain target identified by the MAC address. Therefore, the IP and MAC address should be one-to-one correspondence and their corresponding relations are maintained by the ARP table. ARP attack can use forged information to renewal the ARP table, and destroy the corresponding relations between IP and MAC addresses, which would prevent the communication between the device and the corresponding host. When the IP&MAC Binding function is enabled, the IP and MAC relations in the ARP table won't be expired and renewed automatically, which effectively prevents the ARP attack. Some functions such as access control and bandwidth control, are based on the IP addresses to identify the access clients. The network administrator can allocate every client a static IP, according to which he makes the access and bandwidth rules to control the clients' online behavior and the bandwidth they've used. Some illegal users may change the IP address in order to get higher Internet access. Enabling IP & MAC binding function can effectively prevent the IP embezzlement. NOTE: After IP&MAC binding function is enabled, the IP bound to the MAC cannot be used by other MACs. However this MAC can use other IPs within the same segment, which are not bounded by other MACs, to access the network. - 55 -