Belkin F5D8230-4 User Manual - Page 58
Setting up a Deny Access List
 |
View all Belkin F5D8230-4 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 58 highlights
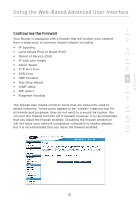
Using the Web-Based Advanced User Interface Setting up a Deny Access List The "Deny Access" list lets you specify computers that you DO NOT want to access the network. Any computer in the list will not be allowed access to the wireless network. All others will. 1. Select the "Deny" radio button (2) to begin setting up a list of computers to be denied access to the wireless network. 2. Next, in the "MAC Address" field that is blank (3), type in the MAC address of the wireless computer you want to deny access to the wireless network, then click "

Using the Web-Based Advanced User Interface
56
Setting up a Deny Access List
The “Deny Access” list lets you specify computers that you DO NOT
want to access the network. Any computer in the list will not be
allowed access to the wireless network. All others will.
1.
Select the “Deny” radio button
(2)
to begin setting up a list of
computers to be denied access to the wireless network.
2.
Next, in the “MAC Address” field that is blank
(3)
, type in the MAC
address of the wireless computer you want to deny access to the
wireless network, then click “<<Add”
(4)
.
3.
Continue to do this until all of the computers you want to deny
access to have been entered.
4.
Click “Apply Changes”
(5)
to finish.