D-Link DSR-250v2 Product Manual - Page 88
IPsec Profiles
 |
View all D-Link DSR-250v2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 88 highlights
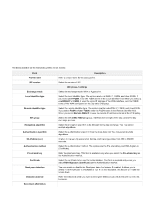
IPsec Profiles The Ipsec profile is the central configuration in IPSec that defines most of the IPSec parameters such as the protocol, algorithms, SA lifetime, and key management protocol. In addition, it contains information related to algorithms such as encryption, authentication, and DH group for Phase I and II negotiations. This section lists all the configured ipsec profiles. The fields displayed on the Ipsec profile table are as follows: Field Name IKE version In use Description It displays the name of the configured ipsec profile. It displays the version of IKE that has been used. It indicates if the configured ipsec profile is being used or not. Click + to add a new entry to the list. This opens the Add Ipsec profiles page. To delete multiple entries, select the checkboxes of the Ipsec profiles you want to delete, and click Delete.