D-Link DSR-250v2 Product Manual - Page 90
Select the local identifier type. The options are Local WAN IP, FQDN, and User-FQDN. If
 |
View all D-Link DSR-250v2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 90 highlights
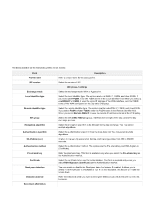
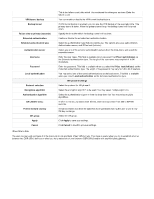
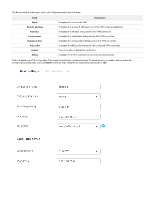
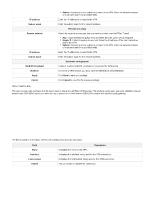
The fields available on the Add Ipsec profiles are as follows: Field Profile name IKE version Exchange mode Local identifier type Remote identifier type DH group Encryption algorithm Authentication algorithm SA lifetime (sec.) Authentication method Pre-shared key Certificate Dead peer detection Detection interval Reconnect after failure Description Enter a unique name for the ipsec profile. Select the version of IKE. IKE phase-1 settings Select the exchange mode: Main or Aggressive. Select the local identifier type. The options are Local WAN IP, FQDN, and User-FQDN. If you select User-FQDN, enter the FQDN name in the Local identifier field. When you select L ocal WAN IP or FQDN, it uses the Local IP address of the WAN interface, and the FQDN name of the WAN configured on the Dynamic DNS page. Select the remote identifier type. The options are Remote WAN IP, FQDN, and User-FQDN. If you select FQDN or User-FQDN, enter the FQDN name in the Remote identifier field. When you select Remote WAN IP, it uses the remote IP address entered in the VPN policy. Select the DH (Diffie-Hellman) group. It defines the strength of the key used in the key exchange process. Select the encryption algorithm to be followed during key exchange. You may select multiple algorithms. Select the authentication algorithm from the drop-down list. You may select multiple algorithms. It refers to the security association lifetime, and the range varies from 300 to 604800 seconds. Select the authentication method. The options are the Pre-shared key and RSA-Signature (Certificate). Enter the preshared key. This field is available only when you select the Pre-shared key as the Authentication method. Select the certificate to be used for authentication. This field is available only when you select RSA-Signature (Certificate) as the Authentication method. You can enable or disable the Dead peer detection feature. If enabled, it allows you to detect if the remote peer is reachable or not. If it is not reachable, this feature will make the tunnel down. Enter the interval at which you want to send peer detection packets to the peer to check its liveliness.