HP Brocade 8/12c Fabric OS Encryption Administrator's Guide - Page 133
Command RBAC permissions and AD types
 |
View all HP Brocade 8/12c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 133 highlights
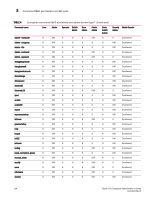
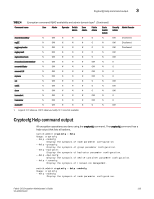
Command RBAC permissions and AD types 3 Command RBAC permissions and AD types Two RBAC roles are permitted to perform Encryption operations. • Admin and SecurityAdmin Users authenticated with the Admin and SecurityAdmin RBAC roles may perform cryptographic functions assigned to the FIPS Crypto Officer, including the following: • Perform encryption node initialization. • Enable cryptographic operations. • Manage I/O functions for critical security parameters (CSPs). • Zeroize encryption CSPs. • Register and configure a key vault. • Configure a recovery share policy. • Create and register recovery share. • Perform encryption group- and clustering-related operations. • Manage keys, including creation, recovery, and archive functions. • Admin and FabricAdmin Users authenticated with the Admin and FabricAdmin RBAC roles may perform routine Encryption Switch management functions, including the following: • Configure virtual devices and crypto LUNs. • Configure LUN and tape associations. • Perform re-keying operations. • Perform firmware download. • Perform regular Fabric OS management functions. See Table 4 for the RBAC permissions when using the encryption configuration commands. TABLE 4 Encryption command RBAC availability and admin domain type1 Command name User Admin Operator Switch Zone Fabric Admin Admin Admin addmembernode addhaclustermember addinitiator addLUN commit create --container create --encgroup create --hacluster create --tapepool N OM N N N O N OM N N N OM N OM N N N OM N OM N N N OM N OM N N N OM N OM N N N OM N OM N N N O N OM N N N OM N OM N N N OM Basic Switch Admin N N N N N N N N N Security Admin Domain Admin OM Disallowed O Disallowed O Disallowed O Disallowed O Disallowed O Disallowed OM Disallowed O Disallowed O Disallowed Fabric OS Encryption Administrator's Guide 113 53-1002159-03