HP Brocade 8/12c Fabric OS Encryption Administrator's Guide - Page 208
Virtual host port 2, through the shared host port, to target port 2
 |
View all HP Brocade 8/12c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 208 highlights
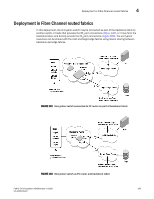
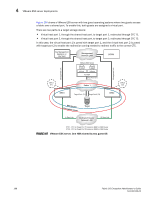
4 VMware ESX server deployments Figure 107 shows a VMware ESX server with two guest operating systems where two guests access a fabric over a shared port. To enable this, both guests are assigned a virtual port. There are two paths to a target storage device: • Virtual host port 1, through the shared host port, to target port 1, redirected through CTC T1. • Virtual host port 2, through the shared host port, to target port 2, redirected through CTC T2. In this case, the virtual host port 1 is zoned with target port 1, and the virtual host port 2 is zoned with target port 2 to enable the redirection zoning needed to redirect traffic to the correct CTC. Key Management Appliance or Key Vault Management Network LAN DCFM CTC1 (T1) Management Link Management Link VMware ESX Server Guest OS1 Guest OS2 V-Port1 V-Port2 FC HBA Host Port1 (I1) Fabric 1 CTC2 (T2) BES1 Target Port1 (T1) Target Port2 (T2) BES4 EncrDypEtKioCnlGusroteurp Target Io Sync Link Dedicated Cluster Network LAN IO Sync Link CTC1 - CTC for Target Port T1 hosted on BES1 in DEK Cluster CTC2 - CTC for Target Port T2 hosted on BES2 in DEK Cluster FIGURE 107 VMware ESX server, One HBA shared by two guest OS 188 Fabric OS Encryption Administrator's Guide 53-1002159-03