HP Brocade 8/12c Fabric OS Encryption Administrator's Guide - Page 48
Registering the SKM or ESKM Brocade group user name and password, Con gt; Encryption
 |
View all HP Brocade 8/12c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 48 highlights
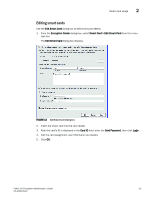
2 Steps for connecting to an SKM or ESKM appliance Registering the SKM or ESKM Brocade group user name and password The Brocade group user name and password you created when configuring a Brocade group on SKM/ESKM must also be registered on each Brocade encryption node. NOTE This operation can be performed only after the switch is added to the encryption group. 1. Select Configure > Encryption from the menu task bar. 2. The Encryption Center dialog box displays. 3. Select a switch from the Encryption Center Devices table, then select Switch > Key Vault Credentials, or right-click a switch and select Key Vault Credentials. The Key Vault Credentials dialog box displays. FIGURE 15 Key Vault Credentials dialog box 4. Enter the Brocade group user name and password. Keep the following rules in mind when registering the Brocade user name and password: - The user name and password must match the user name and password specified for the Brocade group. - The same user name and password must be configured on all nodes in an encryption group. This is not enforced or validated by the encryption group members, so care must be taken when configuring the user name and password to ensure they are the same on each node. - Different user names and passwords can never be used within the same encryption group, but each encryption group may have its own user name and password. - If you change the user name and password, the keys created by the previous user become inaccessible. The Brocade group user name and password must also be changed to the same values on SKM/ESKM to make the keys accessible. - When storage is moved from one encryption group to another, and the new encryption group uses different user name and password, the Brocade group user name and password must also be changed to the same values on SKM/ESKM to make the keys accessible. 5. Repeat the procedure for each node. 28 Fabric OS Encryption Administrator's Guide 53-1002159-03