HP Brocade 8/12c Fabric OS Encryption Administrator's Guide - Page 187
engine of encryption switch 1. Refer to
 |
View all HP Brocade 8/12c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 187 highlights
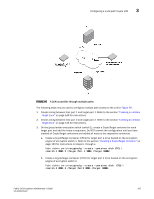
Configuring a multi-path Crypto LUN 3 FIGURE 95 A LUN accessible through multiple paths The following steps may be used to configure multiple path access to the LUN in Figure 95. 1. Create zoning between host port 1 and target port 1. Refer to the section "Creating an initiator - target zone" on page 145 for instructions. 2. Create zoning between host port 2 and target port 2. Refer to the section "Creating an initiator - target zone" on page 145 for instructions. 3. On the group leader encryption switch (switch 1), create a CryptoTarget container for each target port and add the hosts in sequence. Do NOT commit the configuration until you have created all CryptoTarget containers and added all hosts to the respective containers. a. Create a CryptoTarget container (CTC1) for target port 1 to be hosted on the encryption engine of encryption switch 1. Refer to the section "Creating a CryptoTarget container" on page 149 for instructions on steps b. through e. FabricAdmin:switch>cryptocfg --create -container disk CTC1 \ 0 b. Create a CryptoTarget container (CTC2) for target port 2 to be hosted on the encryption engine of encryption switch 2. FabricAdmin:switch>cryptocfg --create -container disk CTC2 \ 0 Fabric OS Encryption Administrator's Guide 167 53-1002159-03