HP dc73 HP Blade Workstation Solution Planning Guide - Page 27
Maximizing RGS security
 |
View all HP dc73 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 27 highlights
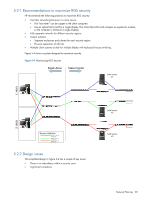
• RGS connections can only be established from the Display Subnet • No RGS Receivers on the Corporate LAN can connect to RGS sessions on the blades. • VPN sessions are likely to come in from the Corporate LAN, limiting external access to blade desktops. • This issue can be fixed by turning on and configuring the link between the data and display LAN switches in the blade enclosure (off by default). 5-2 Maximizing RGS security RGS enables dramatic improvements in data security. In an RGS environment, only display images from the blade workstation are sent to the client computer via the network. The actual application data never leaves the blade workstation. The information that does cross the network (keyboard and mouse events from client, pixels and audio from blade, USB from both) is encrypted with 256-bit AES (Advanced Encryption Standard). The blade workstations themselves can be located in a high-security environment to prevent the physical removal of media or access to I/O ports. With RGS 5.0 and later, HP provides expanded support for remote USB devices. To minimize potential security risks, HP has implemented an Access Control List solution on a group-by-group basis to limit (or eliminate) the USB devices a particular group can mount to the blade workstation from the client. The Blade Workstation Client has recently added Dynamic Domain Name Service (DDNS) with Microsoft Active Directory authentication. Some customers only allow known systems to connect to their network, and maintain that information in Active Directory. In some environments, this may be insufficient. Policies might require physical separation between networks at different security levels to ensure that no data can pass between them. In this case, it may be necessary to use multiple clients with a KVM switch. Network Planning 27