HP dc73 HP Blade Workstation Solution Planning Guide - Page 28
Recommendations to maximize RGS security, 5-2-2 Design issues, User 1, Desk Area, Data Center
 |
View all HP dc73 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
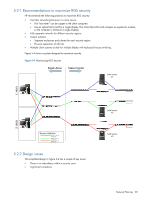
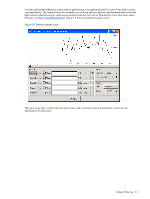
5-2-1 Recommendations to maximize RGS security HP recommends the following practices to maximize RGS security: • Use fiber networking because it is more secure. • The "last meter" can be copper to the client computers • Use an optical LAN card for a single display Thin Client (the LAN card occupies an expansion module, so the computer is limited to a single display) • Fully separate networks for different security regions • System isolation • Separate enclosures and subnets for each security region • Physical separation of all links • Multiple client systems at desk for multiple blades with keyboard/mouse switching. Figure 5-4 shows a system designed to maximize security. Figure 5-4 Maximizing RGS security Desk Area Data Center SAM server #1 User 1 User 2 Secure Subnets 10.1.*.* 10.2.*.* 10.3.*.* 5-2-2 Design issues This simplified design in Figure 5-4 has a couple of key issues: • There is no redundancy within a security zone • Significant complexity SAM server #2 SAM server #3 Network Planning 28