Netgear WNR3500Lv2 User Manual - Page 23
Wireless Security Options, WPA-PSK TKIP, WPA2-PSK AES
 |
View all Netgear WNR3500Lv2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 23 highlights
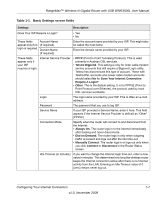
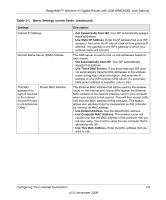
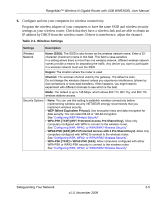
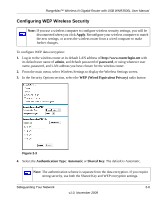
RangeMax™ Wireless-N Gigabit Router with USB WNR3500L User Manual Wireless Security Options Computers can connect over a 802.11g or 802.11n network at a range of up to 300 feet. Such distances can allow for others outside your immediate area to access your network. Unlike wired network data, your wireless data transmissions can extend beyond your walls and can be received by anyone with a compatible adapter. For this reason, use the security features of your wireless equipment. The WNR3500L router provides highly effective security features which are covered in detail in this chapter. Deploy the security features appropriate to your needs. There are several ways you can enhance the security of your wireless network: 1. Open system: Easy, but no security 2. WEP: Security, but some performance impact 3. WPA-PSK: Strong security 4. WPA-2-PSK: Very strong security Figure 2-1 • WEP. Wired Equivalent Privacy (WEP) data encryption provides data security. WEP Shared Key authentication and WEP data encryption block all but the most determined eavesdropper. This data encryption mode has been superseded by WPA-PSK and WPA2-PSK. • WPA-PSK (TKIP), WPA2-PSK (AES). Wi-Fi Protected Access (WPA) using a pre-shared key to perform authentication and generate the initial data encryption keys. The very strong authentication along with dynamic per frame re-keying of WPA makes it virtually impossible to compromise. For more information about wireless technology, see the link to the online document in "Wireless Networking Basics" in Appendix B. Safeguarding Your Network 2-3 v1.0, November 2009