Netgear WNR3500Lv2 User Manual - Page 39
Restricting Access by MAC Address, admin, password, Setup, Access List
 |
View all Netgear WNR3500Lv2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 39 highlights
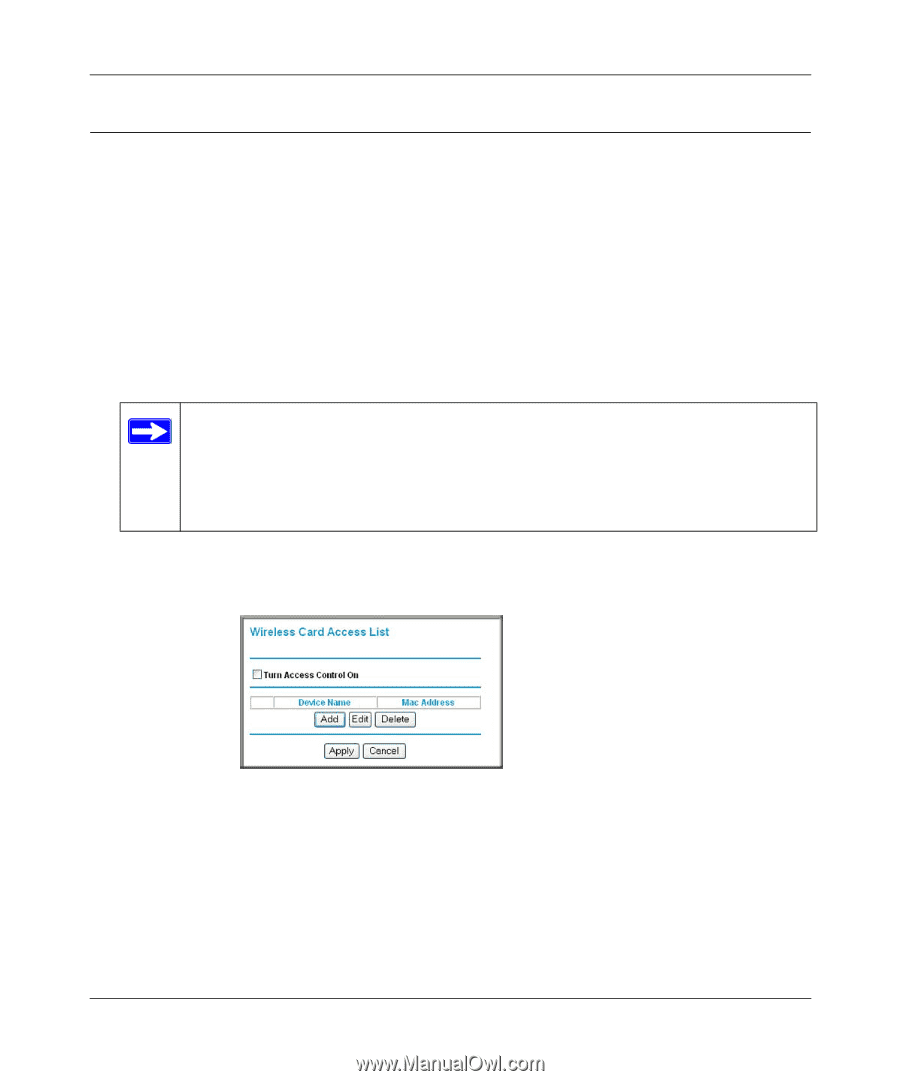
RangeMax™ Wireless-N Gigabit Router with USB WNR3500L User Manual Restricting Access by MAC Address For increased security, you can restrict access to the wireless network to allow only specific PCs based on their MAC addresses. You can restrict access to only trusted PCs so that unknown PCs cannot wirelessly connect to the WNR3500L router. MAC address filtering adds an obstacle against unwanted access to your network, but the data broadcast over the wireless link is fully exposed. To restrict access based on MAC addresses: 1. Log in to the wireless router at its default LAN address of http://www.routerlogin.net with its default user name of admin, and default password of password, or using whatever user name, password, and LAN address you have chosen for the wireless router. Note: If you configure the router from a wireless computer, add your computer's MAC address to the access list. Otherwise you will lose your wireless connection when you click Apply. You must then access the wireless router from a wired computer, or from a wireless computer that is on the access control list, to make any further changes. 2. From Advanced section of the main menu, select Wireless Settings, and then click Setup Access List to display the Wireless Station Access List screen. Figure 3-3 3. Click Add to add a wireless device to the wireless access control list. The Wireless Card Access Setup screen opens and displays a list of currently active wireless cards and their MAC addresses. Protecting Your Network 3-3 v1.0, November 2009