Netgear FWAG114 FWAG114 Reference Manual - Page 52
Inbound Rule Example: Allowing Videoconference from Restricted Addresses, Considerations for Inbound
 |
UPC - 606449026955
View all Netgear FWAG114 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 52 highlights
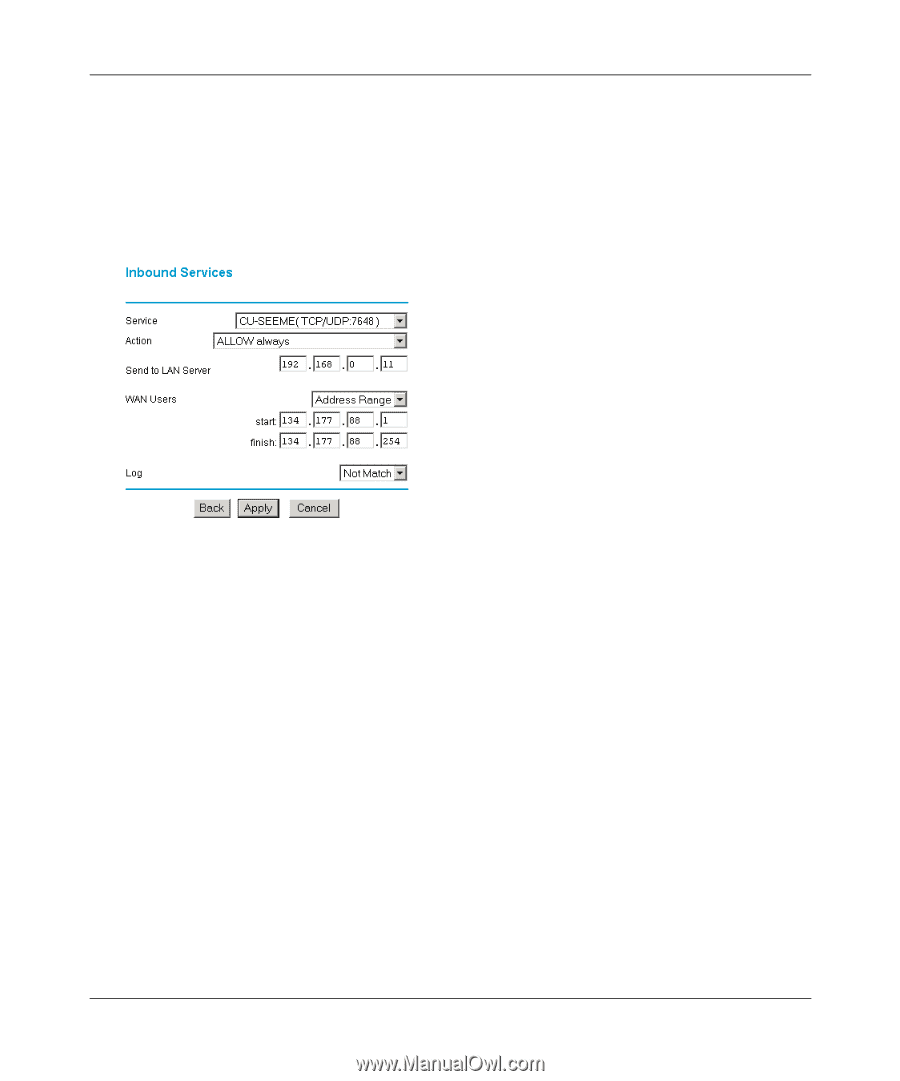
Reference Manual for the ProSafe Dual Band Wireless VPN Firewall FWAG114 Inbound Rule Example: Allowing Videoconference from Restricted Addresses If you want to allow incoming videoconferencing to be initiated from a restricted range of outside IP addresses, such as from a branch office, you can create an inbound rule. In the example shown in Figure 5-4, CU-SeeMe connections are allowed only from a specified range of external IP addresses. In this case, we have also specified logging of any incoming CU-SeeMe requests that do not match the allowed parameters. Figure 5-4: Rule example: Videoconference from Restricted Addresses Considerations for Inbound Rules • If your external IP address is assigned dynamically by your ISP, the IP address may change periodically as the DHCP lease expires. Consider using the Dyamic DNS feature in the Advanced menus so that external users can always find your network. • If the IP address of the local server PC is assigned by DHCP, it may change when the PC is rebooted. To avoid this, use the Reserved IP address feature in the LAN IP menu to keep the PC's IP address constant. • Local PCs must access the local server using the PCs' local LAN address (192.168.0.99 in this example). Attempts by local PCs to access the server using the external WAN IP address will fail. 5-6 Firewall Protection and Content Filtering