Netgear FWAG114 FWAG114 Reference Manual - Page 74
Using Policies to Manage VPN Traffic, Using Automatic Key Management
 |
UPC - 606449026955
View all Netgear FWAG114 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 74 highlights
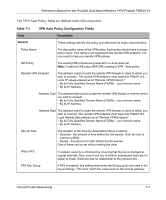
Reference Manual for the ProSafe Dual Band Wireless VPN Firewall FWAG114 Using Policies to Manage VPN Traffic You create policy definitions to manage VPN traffic on the FWAG114. There are two kinds of policies: • IKE Policies: Define the authentication scheme and automatically generate the encryption keys. As an alternative option, to further automate the process, you can create an IKE policy which uses a trusted certificate authority to provide the authentication while the IKE policy still handles the encryption. • VPN Policies: Apply the IKE policy to specific traffic which requires a VPN tunnel. Or, you can create a VPN policy which does not use an IKE policy but in which you manually enter all the authentication and key parameters. Since the VPN policies use the IKE policies, you define the IKE policy first. The FWAG114 also allows you to manually input the authentication scheme and encryption key values. In the case of manual key management there will not be any IKE policies. In order to establish secure communication over the Internet with the remote site you need to configure matching VPN policies on both the local and remote FWAG114 wireless firewalls. The outbound VPN policy on one end must match to the inbound VPN policy on other end, and vice versa. When the network traffic enters into the FWAG114 from the LAN network interface, if there is no VPN policy found for a type of network traffic, then that traffic passes through without any change. However, if the traffic is selected by a VPN policy, then the IPSec authentication and encryption rules will be applied to it as defined in the VPN policy. By default, a new VPN policy is added with the least priority, that is, at the end of the VPN policy table. Using Automatic Key Management The most common configuration scenarios will use IKE policies to automatically manage the authentication and encryption keys. Based on the IKE policy, some parameters for the VPN tunnel are generated automatically. The IKE protocols perform negotiations between the two VPN endpoints to automatically generate required parameters. Some organizations will use an IKE policy with a Certificate Authority (CA) to perform authentication. Typically, CA authentication is used in large organizations which maintain their own internal CA server. This requires that each VPN gateway has a certificate from the CA. Using CAs reduces the amount of data entry required on each VPN endpoint. 7-2 Virtual Private Networking