Netgear WNR1000v3 User Manual - Page 28
Safeguarding Your Network, Choosing Appropriate Wireless Security - firewall
 |
View all Netgear WNR1000v3 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
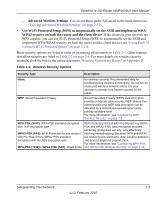
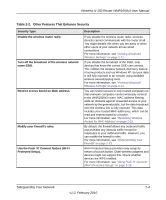
Chapter 2 Safeguarding Your Network The Wireless-N 150 Router Model WNR1000v3 provides highly effective security features, which are covered in detail in this chapter. This chapter includes the following sections: • "Choosing Appropriate Wireless Security" • "Recording Basic Wireless Settings Setup Information" on page 2-5 • "Changing Wireless Security Settings" on page 2-6 • "Viewing Advanced Wireless Settings" on page 2-11 • "Using Push 'N' Connect (Wi-Fi Protected Setup)" on page 2-13 • "Restricting Wireless Access by MAC Address" on page 2-18 • "Adding Guest Networks" on page 2-20 • "Changing the Administrator Password" on page 2-22 • "Backing Up Your Configuration" on page 2-23 • "Understanding Your Firewall" on page 2-23 Choosing Appropriate Wireless Security Unlike wired networks, wireless networks allow anyone with a compatible adapter to receive your wireless data transmissions well beyond your walls. Operating an unsecured wireless network creates an opportunity for outsiders to eavesdrop on your network traffic or to enter your network to access your computers and files. Indoors, computers can connect over wireless networks at ranges of up to 300 feet. Such distances can allow for others outside your immediate area to access your network. Use the security features of your wireless equipment that are appropriate to your needs. The time it takes to establish a wireless connection can vary depending on both your security settings and router placement. 2-1 v1.0, February 2010