D-Link DFL-300 User Manual - Page 150
Log, The FIREWALL VPN ROUTER Office Firewall supports traffic logging - vpn setup
 |
UPC - 790069240751
View all D-Link DFL-300 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 150 highlights
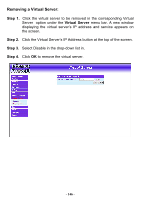
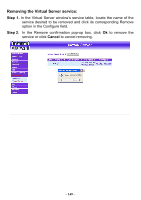
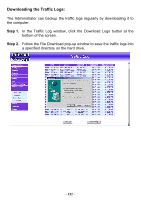
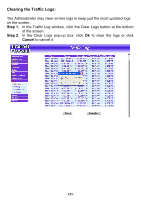
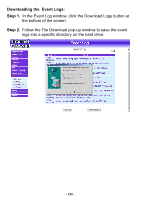
Log The FIREWALL VPN ROUTER Office Firewall supports traffic logging and event logging to monitor and record services, connection times, and the source and destination network address. The Administrator may also download the log files for backup purposes. The Administrator mainly uses the Log menu to monitor the traffic passing through the FIREWALL VPN ROUTER Firewall. What is Log? Log records all connections that pass through the Firewall's control policies. Traffic log's parameters are setup when setting up control policies. Traffic logs record the details of packets such as the start and stop time of connection, the duration of connection, the source address, the destination address and services requested, for each control policy. Event logs record the contents of System Configuration changes made by the Administrator such as the time of change, settings that change, the IP address used to log on, etc. How to use the Log The Administrator can use the log data to monitor and manage the FIREWALL VPN ROUTER and the networks. The Administrator can view the logged data to evaluate and troubleshoot the network, such as pinpointing the source of traffic congestions. - 150 -