D-Link DFL-300 User Manual - Page 88
Policy, What is Policy?, How do I use Policy?
 |
UPC - 790069240751
View all D-Link DFL-300 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 88 highlights
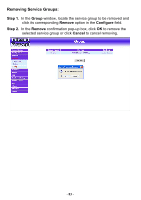
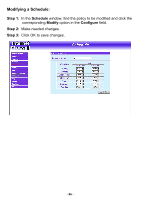
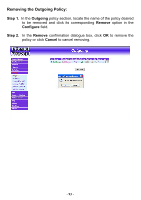
Policy This section provides the Administrator with facilities to sent control policies for packets with different source IP addresses, source ports, destination IP addresses, and destination ports. Control policies decide whether packets from different network objects, network services, and applications are able to pass through the Firewall. What is Policy? The FIREWALL VPN ROUTER uses policies to filter packets. The policy settings are: source address, destination address, services, permission, packet log, packet statistics, and flow alarm. Based on its source addresses, a packet can be categorized into: (1). Outgoing: a client is in the internal networks while a server is in the external networks. (2) Incoming, a client is in the external networks, while a server is in the internal networks. (3) To DMZ: a client is either in the internal networks or in the external networks while, server is in DMZ. (4) From DMZ, a client is in DMZ while server is either in the internal networks or in the external networks. How do I use Policy? The policy settings are source addresses, destination addresses, services, permission, log, statistics, and flow alarm. Among them, source addresses, destination addresses and IP mapping addresses have to be defined in the Address menu in advance. Services can be used directly in setting up policies, if they are in the Pre-defined Service menu. Custom services need to be defined in the Custom menu before they can be used in the policy settings. If the destination address of an incoming policy is a Mapped IP address or a Virtual Server address, then the address has to be defined in the Virtual Server section instead of the Address section. Policy Directions: Step 1. Step 2. Step 3. Step 4. In Address, set names and addresses of source networks and destination networks. In Service, set services. In Virtual Server, set names and addresses of mapped IP or virtual server (only applied to Incoming policies). Set control policies in Policy - 88 -