HP 6125XLG R2306-HP 6125XLG Blade Switch ACL and QoS Configuration Guide - Page 41
Traffic policing,
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 41 highlights
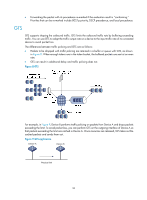
CBS is implemented with bucket C, and EBS with bucket E. When only the CIR is used for traffic evaluation, packets are measured against the following bucket scenarios: • If bucket C has enough tokens, packets are colored green. • If bucket C does not have enough tokens but bucket E has enough tokens, packets are colored yellow. • If neither bucket C nor bucket E has sufficient tokens, packets are colored red. When both CIR and PIR are used to evaluate traffic, bucket P, which is equal to the sum of the CBS and EBS in size, is introduced. In this case, packets are measured against the following bucket scenarios: • If both bucket C and bucket P have enough tokens, packets are colored green. • If bucket C does not have enough tokens but bucket P has enough tokens, packets are colored yellow. • If bucket P does not have enough tokens, packets are colored red. You can configure traffic control policies for packets of different colors by using the traffic policing feature. Traffic policing Traffic policing supports policing the inbound traffic and the outbound traffic. A typical application of traffic policing is to supervise the specification of certain traffic entering a network and limit it within a reasonable range, or to "discipline" the extra traffic to prevent aggressive use of network resources by a certain application. For example, you can limit bandwidth for HTTP packets to less than 50% of the total. If the traffic of a certain session exceeds the limit, traffic policing can drop the packets or reset the IP precedence of the packets. Figure 7 shows an example of policing outbound traffic on an interface. Figure 7 Traffic policing Traffic policing is widely used in policing traffic entering the networks of ISPs. It can classify the policed traffic and take pre-defined policing actions on each packet depending on the evaluation result: • Forwarding the packet if the evaluation result is "conforming." • Dropping the packet if the evaluation result is "excess." 35