TRENDnet TEW-453APB User Guide - Page 32
Security Settings - WPA-802.1x, WPA-802.1x Wireless Security
 |
UPC - 710931502732
View all TRENDnet TEW-453APB manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 32 highlights
Access Point Setup Security Settings - WPA-802.1x This version of WPA requires a Radius Server on your LAN to provide the client authentication according to the 802.1x standard. Data transmissions are encrypted using the WPA standard. If this option is selected: • This Access Point must have a "client login" on the Radius Server. • Each user must have a "user login" on the Radius Server. Normally, a Certificate is used to authenticate each user. See Chapter4 for details of user configuration. • Each user's wireless client must support 802.1x. • All data transmission is encrypted using the WPA standard. Keys are automatically generated, so no key input is required. Figure 18: WPA-802.1x Wireless Security 29
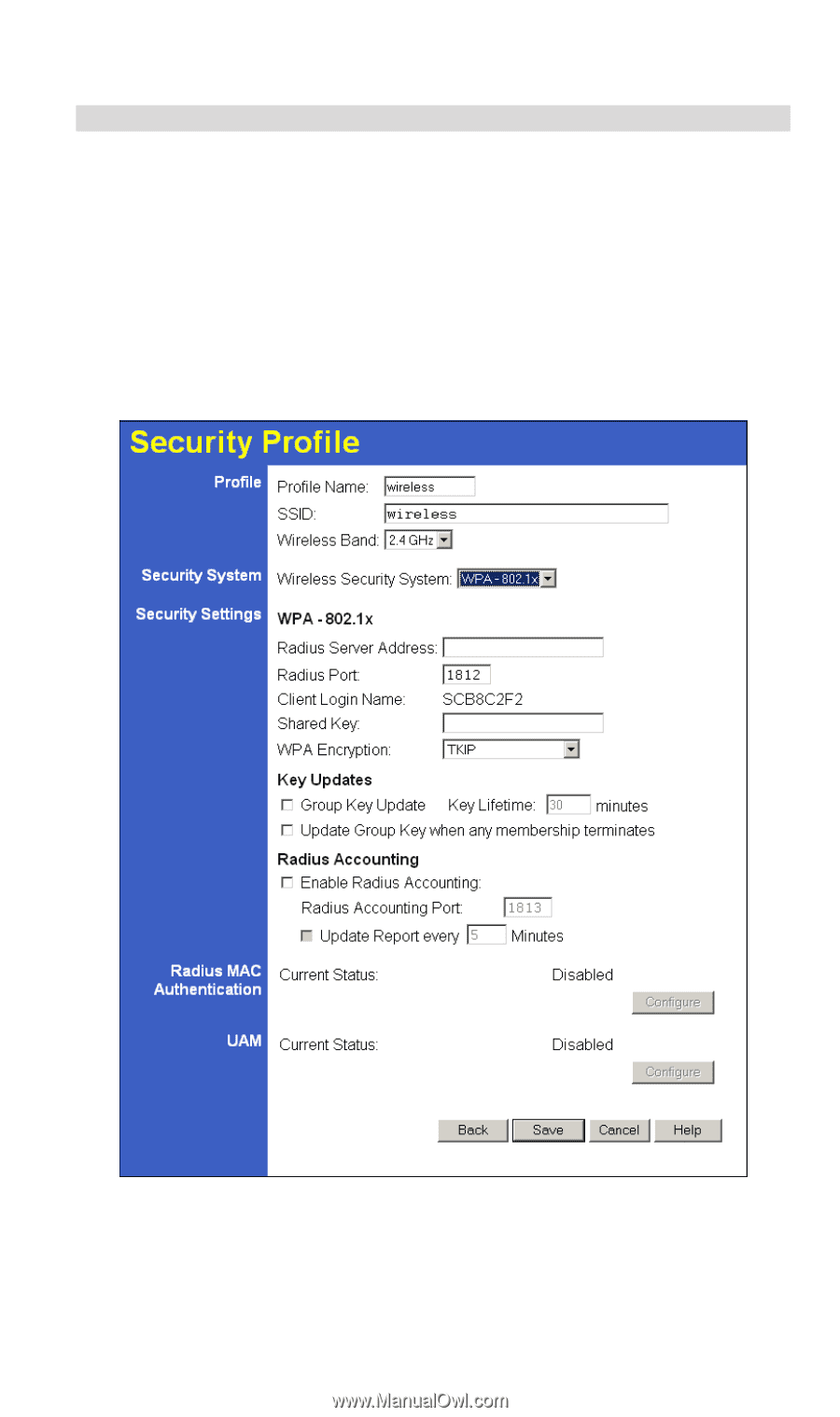
Access Point Setup
Security Settings - WPA-802.1x
This version of WPA requires a Radius Server on your LAN to provide the client authentica-
tion according to the 802.1x standard. Data transmissions are encrypted using the WPA
standard.
If this option is selected:
•
This Access Point must have a "client login" on the Radius Server.
•
Each user must have a "user login" on the Radius Server. Normally, a Certificate is used to
authenticate each user. See Chapter4 for details of user configuration.
•
Each user's wireless client must support 802.1x.
•
All data transmission is encrypted using the WPA standard. Keys are automatically
generated, so no key input is required.
Figure 18: WPA-802.1x Wireless Security
29