ZyXEL G-220 User Guide - Page 108
Security Parameters Summary, ZyXEL G-220 v2 User's Guide, Appendix D Wireless Security
 |
View all ZyXEL G-220 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 108 highlights
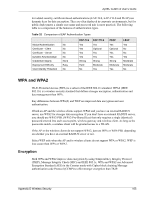
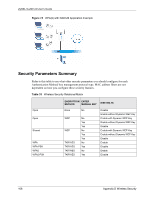
ZyXEL G-220 v2 User's Guide Figure 74 WPA(2) with RADIUS Application Example Security Parameters Summary Refer to this table to see what other security parameters you should configure for each Authentication Method/ key management protocol type. MAC address filters are not dependent on how you configure these security features. Table 33 Wireless Security Relational Matrix AUTHENTICATION METHOD/ KEY MANAGEMENT PROTOCOL ENCRYPTION METHOD ENTER MANUAL KEY Open None No Open Shared WPA WPA-PSK WPA2 WPA2-PSK WEP No Yes Yes WEP No Yes Yes TKIP/AES No TKIP/AES Yes TKIP/AES No TKIP/AES Yes IEEE 802.1X Disable Enable without Dynamic WEP Key Enable with Dynamic WEP Key Enable without Dynamic WEP Key Disable Enable with Dynamic WEP Key Enable without Dynamic WEP Key Disable Enable Disable Enable Disable 108 Appendix D Wireless Security