ZyXEL P-2802HW-I1 User Guide - Page 191
ID Type and Content
 |
View all ZyXEL P-2802HW-I1 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 191 highlights
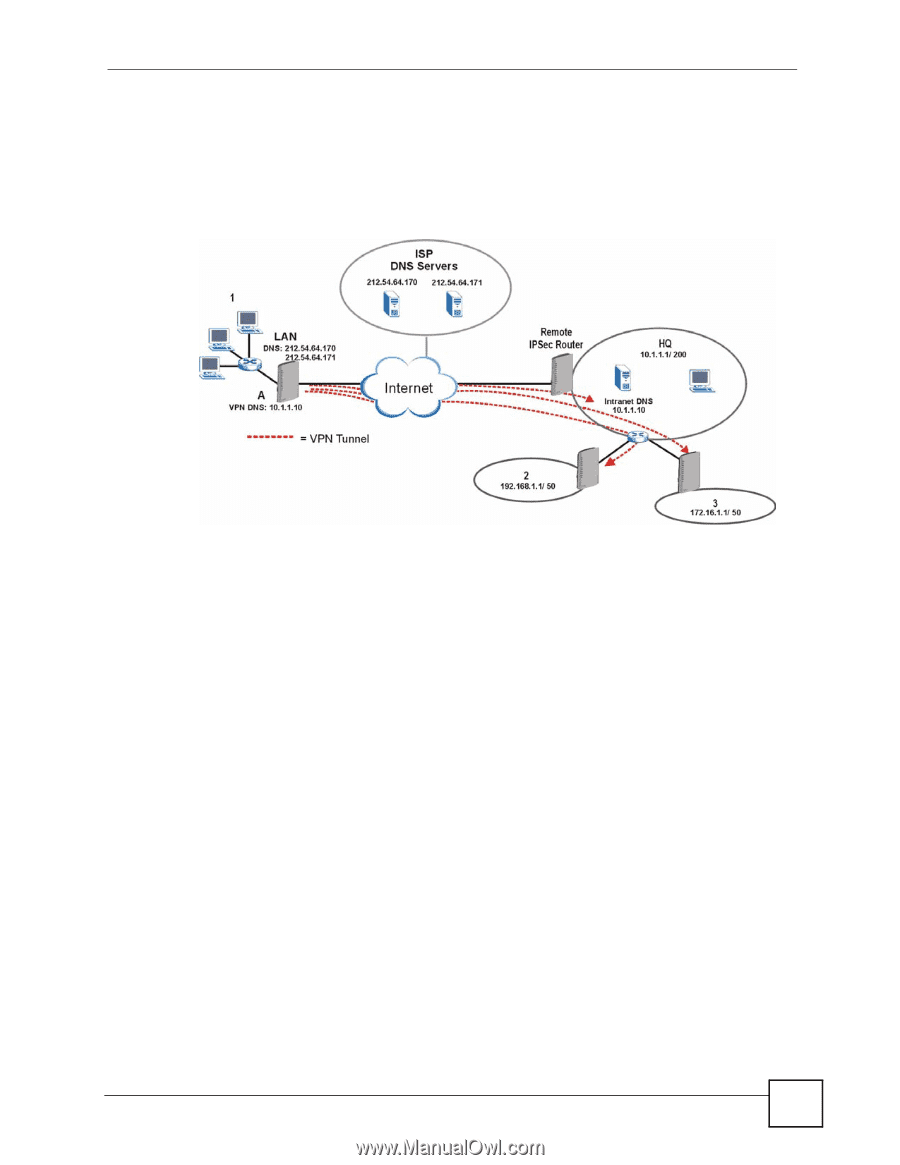
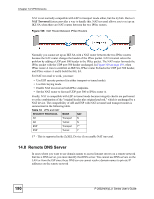
Chapter 14 VPN Screens The following figure depicts an example where three VPN tunnels are created from ZyXEL Device A; one to branch office 2, one to branch office 3 and another to headquarters. In order to access computers that use private domain names on the headquarters (HQ) network, the ZyXEL Device at branch office 1 uses the Intranet DNS server in headquarters. The DNS server feature for VPN does not work with Windows 2000 or Windows XP. Figure 109 VPN Host using Intranet DNS Server Example If you do not specify an Intranet DNS server on the remote network, then the VPN host must use IP addresses to access the computers on the remote network. 14.9 ID Type and Content With aggressive negotiation mode (seeSection 14.12.1 on page 199), the ZyXEL Device identifies incoming SAs by ID type and content since this identifying information is not encrypted. This enables the ZyXEL Device to distinguish between multiple rules for SAs that connect from remote IPSec routers that have dynamic WAN IP addresses. Telecommuters can use separate passwords to simultaneously connect to the ZyXEL Device from IPSec routers with dynamic IP addresses (seeSection 14.18 on page 207 for a telecommuter configuration example). Regardless of the ID type and content configuration, the ZyXEL Device does not allow you to save multiple active rules with overlapping local and remote IP addresses. With main mode (seeSection 14.12.1 on page 199), the ID type and content are encrypted to provide identity protection. In this case the ZyXEL Device can only distinguish between up to 12 different incoming SAs that connect from remote IPSec routers that have dynamic WAN IP addresses. The ZyXEL Device can distinguish up to 12 incoming SAs because you can select between three encryption algorithms (DES, 3DES and AES), two authentication algorithms (MD5 and SHA1) and two key groups (DH1 and DH2) when you configure a VPN rule (seeSection 14.13 on page 200). The ID type and content act as an extra level of identification for incoming SAs. The type of ID can be a domain name, an IP address or an e-mail address. The content is the IP address, domain name, or e-mail address. P-2802H(W)(L)-I Series User's Guide 191