Belkin F5D7234-4 Version 4xxx User Manual - Page 66
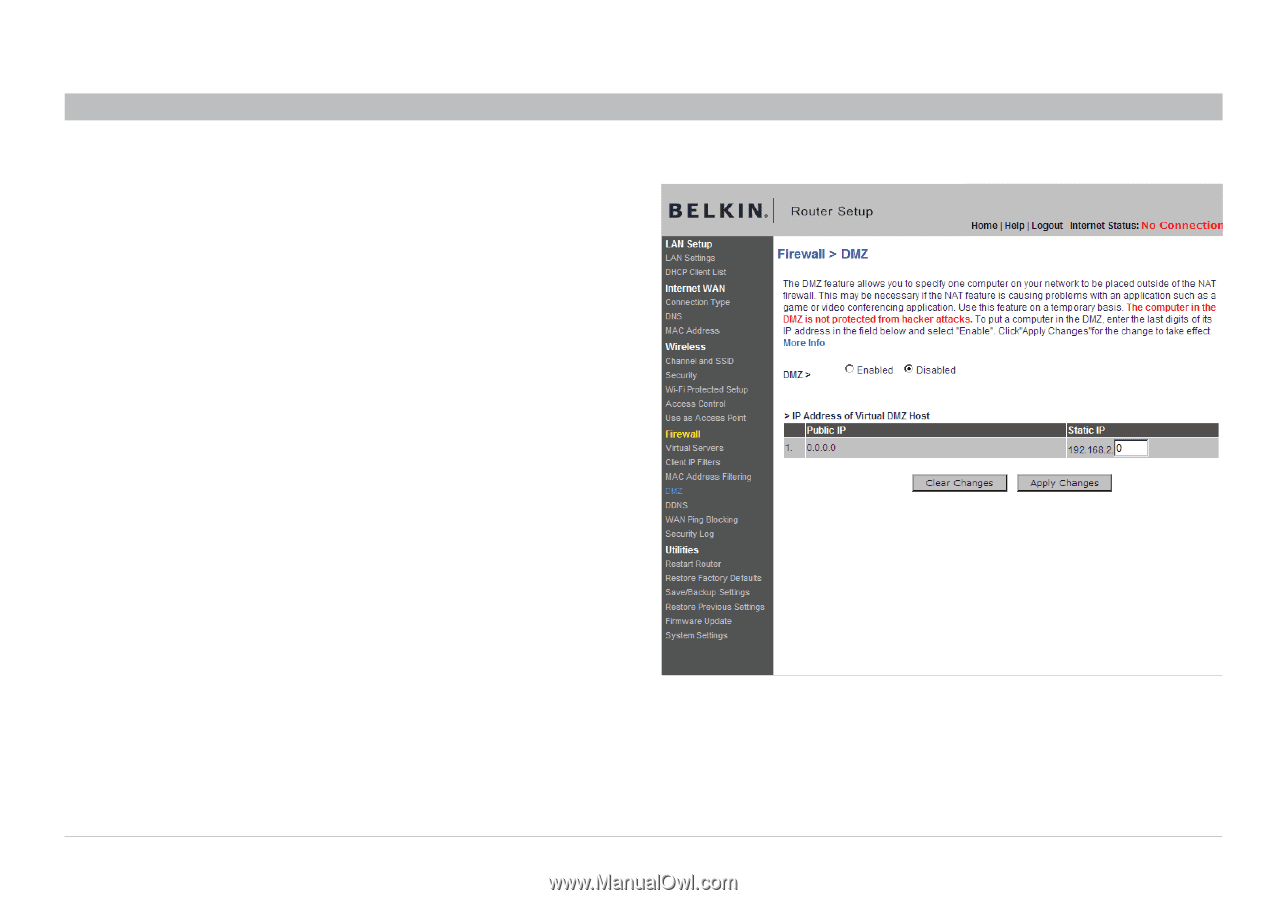
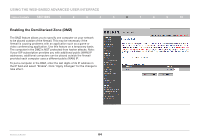
Enabling the Demilitarized Zone DMZ
 |
UPC - 722868680599
View all Belkin F5D7234-4 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 66 highlights
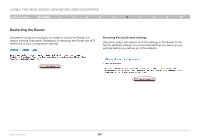
Using the Web-Based Advanced User Interface Table of Contents sections 1 2 3 4 5 6 7 8 9 10 Enabling the Demilitarized Zone (DMZ) The DMZ feature allows you to specify one computer on your network to be placed outside of the firewall. This may be necessary if the firewall is causing problems with an application such as a game or video conferencing application. Use this feature on a temporary basis. The computer in the DMZ is NOT protected from hacker attacks. Note: If your ISP subscription provides you with additional public (WAN) IP addresses, additional computers can be placed outside the firewall provided each computer uses a different public (WAN) IP. To put a computer in the DMZ, enter the last digits of its IP address in the IP field and select "Enable". Click "Apply Changes" for the change to take effect. To put a computer in the DMZ, enter the last digits of its IP address in the IP field and select "Enable". Click "Apply Changes" for the change to take effect. Wireless G Router 64