ZyXEL ZYWALL USG 100 User Guide - Page 65
VPN Concentrator Example, Branch Office
 |
View all ZyXEL ZYWALL USG 100 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 65 highlights
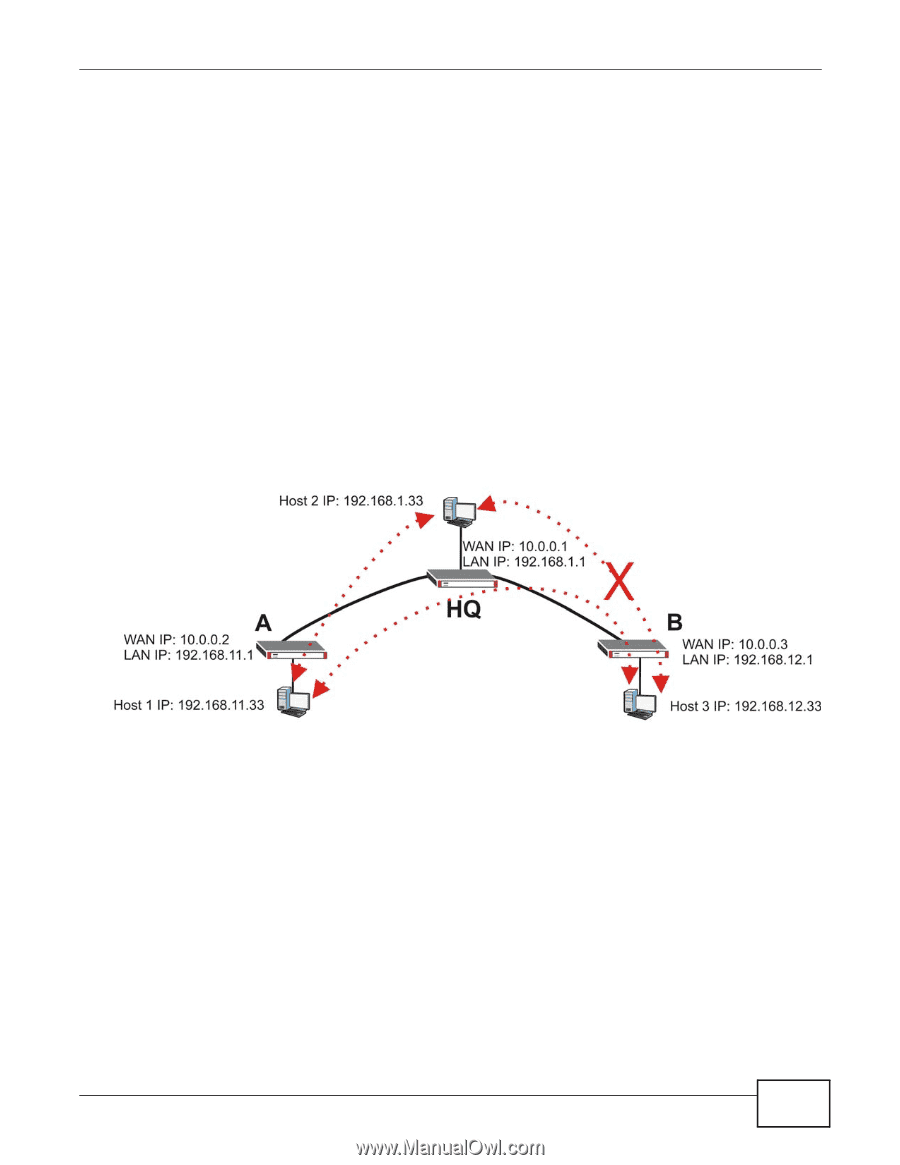
Chapter 4 Create Secure Connections Across the Internet • Multiple SAs connecting through a secure gateway must have the same negotiation mode. If you have the Configuration > VPN > IPSec VPN > VPN Connection screen's Use Policy Route to control dynamic IPSec rules option enabled and the VPN connection is up but VPN traffic cannot be transmitted through the VPN tunnel, check the routing policies to see if they are sending traffic elsewhere instead of through the VPN tunnels. 4.2 VPN Concentrator Example A VPN concentrator uses hub-and-spoke VPN topology to combine multiple IPSec VPN connections into one secure network. The hub routes VPN traffic between the spoke routers and itself. This reduces the number of VPN connections to set up and maintain. Here a VPN concentrator connects ZLD-based ZyWALLs at headquarters (HQ) and branch offices A and B in one secure network. • Branch A's ZyWALL uses one VPN rule to access both the headquarters (HQ) network and branch B's network. • Branch B's ZyWALL uses one VPN rule to access branch A's network only. Branch B is not permitted to access the headquarters network. Figure 27 IPSec VPN Concentrator Example This IPSec VPN concentrator example uses the following settings. Branch Office A VPN Gateway (VPN Tunnel 1): • My Address: 10.0.0.2 • Peer Gateway Address: 10.0.0.1 VPN Connection (VPN Tunnel 1): • Local Policy: 192.168.11.0/255.255.255.0 • Remote Policy: 192.168.1.0/255.255.255.0 • Disable Policy Enforcement Policy Route ZyWALL USG100-PLUS User's Guide 65