Dell PowerVault TL4000 Dell PowerVault ML6000 Encryption Key Manager User's - Page 15
Manager fetches the required key from the keystore, based on the information
 |
View all Dell PowerVault TL4000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 15 highlights
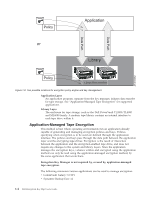
locations within an enterprise. A command line interface client provides a robust set of commands to customize the Encryption Key Manager for your environment and monitor its operation. Many customization and monitoring functions are also available on the Dell Encryption Key Manager graphical user interface (GUI). The Encryption Key Manager uses one or more keystores to hold the certificates and keys (or pointers to the certificates and keys) required for all encryption tasks. See "Keystore Considerations" on page 2-3 for detailed information. IMPORTANT Encryption Key Manager HOST SERVER CONFIGURATION INFORMATION: It is recommended that machines hosting the Dell Encryption Key Manager program use ECC memory in order to minimize the risk of data loss. The Encryption Key Manager performs the function of requesting the generation of encryption keys and passing those keys to the | LTO 4 and LTO 5 tape drives. The key material, in wrapped (encrypted form) resides in system memory during processing by the Encryption Key Manager. Note that the key material must be transferred without error to the appropriate tape drive so that data written on a cartridge may be recovered (decrypted). If for some reason key material is corrupted due to a bit error in system memory, and that key material is used to write data to a cartridge, then the data written to that cartridge will not be recoverable (i.e. decrypted at a later date). There are safeguards in place to make sure that such data errors do not occur. However, if the machine hosting the Encryption Key Manager is not using Error Correction Code (ECC) memory there remains a possibility that the key material may become corrupted while in system memory and the corruption could then cause data loss. The chance of this occurrence is small, but it is always recommended that machines hosting critical applications (like the Encryption Key Manager) use ECC memory. The Encryption Key Manager acts as a background process awaiting key generation or key retrieval requests sent to it through a TCP/IP communication path between itself and the tape library. When a tape drive writes encrypted data, it first requests an encryption key from the Encryption Key Manager. Upon receipt of the request, the Encryption Key Manager performs the following tasks. The Encryption Key Manager fetches an existing AES key from a keystore and wraps it for secure transfer to the tape drive where it is unwrapped upon arrival and used to encrypt the data being written to tape. | When an encrypted tape is read by an LTO 4 or LTO 5 drive, the Encryption Key Manager fetches the required key from the keystore, based on the information in the Key ID on the tape, and serves it to the tape drive wrapped for secure transfer. There are two methods of encryption management to choose from. These methods differ in where the encryption policy engine resides, where key management is performed for your solution, as well as how the Encryption Key Manager is connected to the drive. Your operating environment determines which is the best for you. Key management and the encryption policy engine may be located in any one of the following two environmental layers. Chapter 1. Tape Encryption Overview 1-3