Dell PowerVault TL4000 Dell PowerVault ML6000 Encryption Key Manager User's - Page 16
Application-Managed Tape Encryption - user s guide
 |
View all Dell PowerVault TL4000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 16 highlights
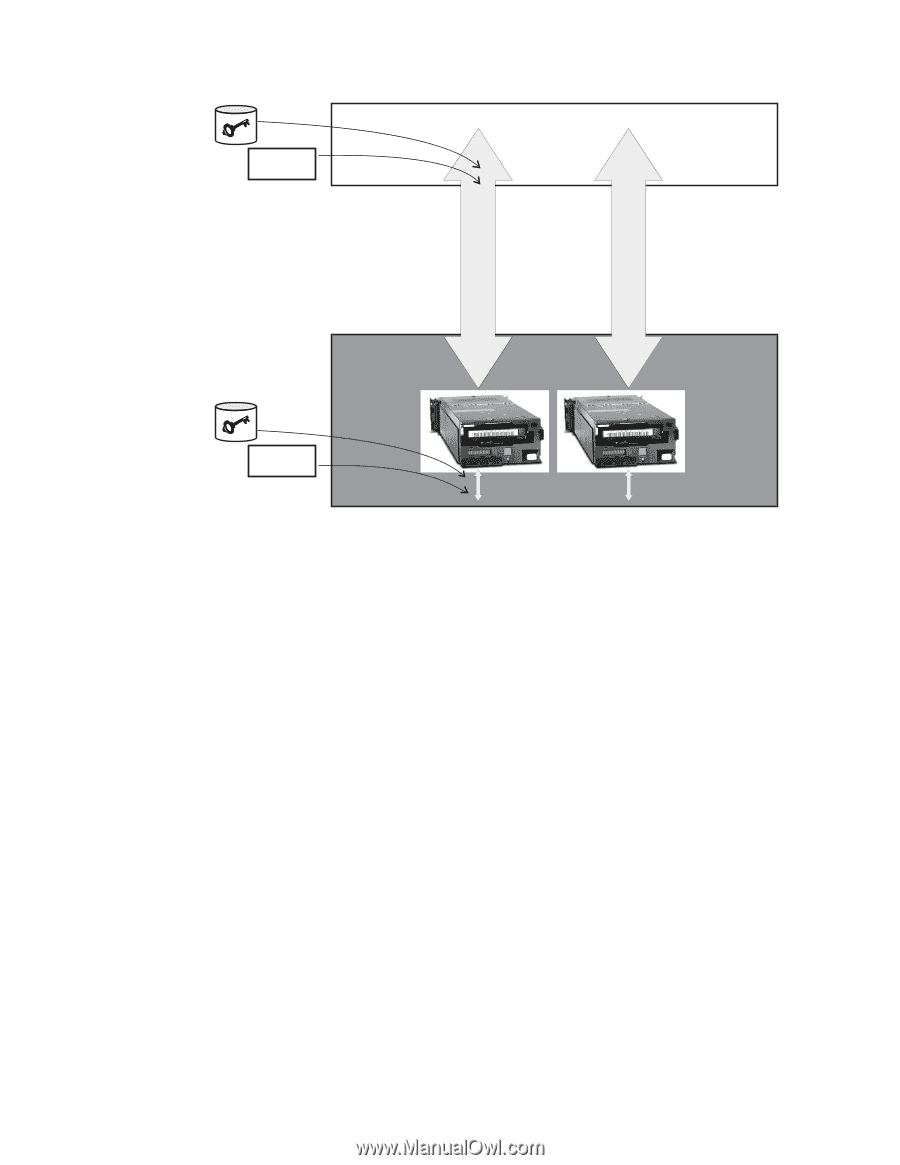
Data Path Data Path Policy or Application Library a14m0252 Policy Library Drive Interface Figure 1-2. Two possible locations for encryption policy engine and key management. Application Layer An application program, separate from the key manager, initiates data transfer for tape storage. See "Application-Managed Tape Encryption" for supported applications. Library Layer The enclosure for tape storage, such as the Dell PowerVault TL2000/TL4000 and ML6000 family. A modern tape library contains an internal interface to each tape drive within it. Application-Managed Tape Encryption This method is best where operating environments run an application already capable of generating and managing encryption policies and keys. Policies specifying when encryption is to be used are defined through the application interface. The policies and keys pass through the data path between the application layer and the encrypting tape drives. Encryption is the result of interaction between the application and the encryption-enabled tape drive, and does not require any changes to the system and library layers. Since the application manages the encryption keys, volumes written and encrypted using the application method can only be read using the application-managed encryption method, by the same application that wrote them. Encryption Key Manager is not required by, or used by, application-managed tape encryption. The following minimum version applications can be used to manage encryption: v CommVault Galaxy 7.0 SP1 v Symantec Backup Exec 12 1-4 Dell Encryption Key Mgr User's Guide