Netgear STM300 STM 150-300-600 Reference Manual (PDF) - Page 38
Table 7., Setup Wizard Step 4: Email Security Settings
 |
UPC - 606449062458
View all Netgear STM300 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
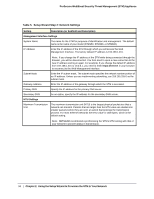
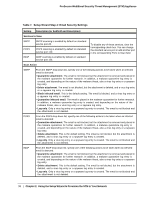
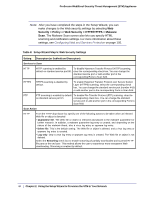
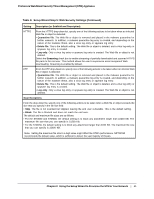
ProSecure Web/Email Security Threat Management (STM) Appliance Table 7. Setup Wizard Step 4: Email Security Settings Setting Description (or Subfield and Description) Services to Scan SMTP POP3 IMAP SMTP scanning is enabled by default on standard service port 25. POP3 scanning is enabled by default on standard service port 110. IMAP scanning is enabled by default on standard service port 143. To disable any of these services, clear the corresponding check box. You can change the standard service port or add another port in the corresponding Ports to Scan field. Scan Action SMTP From the SMTP drop-down list, specify one of the following actions to be taken when an infected email is detected: • Quarantine attachment. The email is not blocked, but the attachment is removed and placed in the malware quarantine for further research. In addition, a malware quarantine log entry is created, and depending on the nature of the malware threat, also a virus log entry or a spyware log entry. • Delete attachment. The email is not blocked, but the attachment is deleted, and a virus log entry or a spyware log entry is created. • Block infected email. This is the default setting. The email is blocked, and a virus log entry or a spyware log entry is created. • Quarantine infected email. The email is placed in the malware quarantine for further research. In addition, a malware quarantine log entry is created, and depending on the nature of the malware threat, also a virus log entry or a spyware log entry. • Log only. Only a virus log entry or a spyware log entry is created. The email is not blocked and the attachment is not deleted. POP3 From the POP3 drop-down list, specify one of the following actions to be taken when an infected email is detected: • Quarantine attachment. The email is not blocked, but the attachment is removed and placed in the malware quarantine for further research. In addition, a malware quarantine log entry is created, and depending on the nature of the malware threat, also a virus log entry or a spyware log entry. • Delete attachment. This is the default setting. The email is not blocked, but the attachment is deleted, and a virus log entry or a spyware log entry is created. • Log only. Only a virus log entry or a spyware log entry is created. The email is not blocked and the attachment is not deleted. IMAP From the IMAP drop-down list, specify one of the following actions to be taken when an infected email is detected: • Quarantine attachment. The email is not blocked, but the attachment is removed and placed in the malware quarantine for further research. In addition, a malware quarantine log entry is created, and depending on the nature of the malware threat, also a virus log entry or a spyware log entry. • Delete attachment. This is the default setting. The email is not blocked, but the attachment is deleted, and a virus log entry or a spyware log entry is created. • Log only. Only a virus log entry or a spyware log entry is created. The email is not blocked and the attachment is not deleted. 38 | Chapter 2. Using the Setup Wizard to Provision the STM in Your Network