Netgear STM300 STM 150-300-600 Reference Manual (PDF) - Page 40
Security > Policy, Web Security > HTTP/HTTPS > Malware, Table 8.
 |
UPC - 606449062458
View all Netgear STM300 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 40 highlights
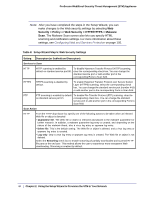
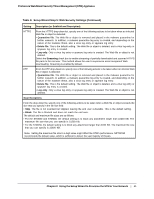
ProSecure Web/Email Security Threat Management (STM) Appliance Note: After you have completed the steps in the Setup Wizard, you can make changes to the Web security settings by selecting Web Security > Policy or Web Security > HTTP/HTTPS > Malware Scan. The Malware Scan screen also lets you specify HTML scanning and notification settings. For more information about these settings, see Configuring Web and Services Protection on page 105. Table 8. Setup Wizard Step 5: Web Security Settings Setting Description (or Subfield and Description) Services to Scan HTTP HTTP scanning is enabled by default on standard service port 80. To disable Hypertext Transfer Protocol (HTTP) scanning, clear the corresponding check box. You can change the standard service port or add another port in the corresponding Ports to Scan field. HTTPS HTTPS scanning is disabled by default. To enable Hypertext Transfer Protocol over Secure Socket Layer (HTTPS) scanning, select the corresponding check box. You can change the standard service port (number 443) or add another port in the corresponding Ports to Scan field. FTP FTP scanning is enabled by default To disable File Transfer Protocol (FTP) scanning, clear the on standard service port 21. corresponding check box. You can change the standard service port or add another port in the corresponding Ports to Scan field. Scan Action HTTP From the HTTP drop-down list, specify one of the following actions to be taken when an infected Web file or object is detected: • Quarantine file. The Web file or object is removed and placed in the malware quarantine for further research. In addition, a malware quarantine log entry is created, and depending on the nature of the malware threat, also a virus log entry or spyware log entry. • Delete file. This is the default setting. The Web file or object is deleted, and a virus log entry or spyware log entry is created. • Log only. Only a virus log entry or spyware log entry is created. The Web file or object is not deleted. Select the Streaming check box to enable streaming of partially downloaded and scanned HTTP file parts to the end user. This method allows the user to experience more transparent Web downloading. Streaming is enabled by default. 40 | Chapter 2. Using the Setup Wizard to Provision the STM in Your Network