HP Jetdirect 200m HP Jetdirect 200m Print Server (English) User Guide - Page 23
Wireless security, Network name SSID, Authentication
 |
View all HP Jetdirect 200m manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 23 highlights
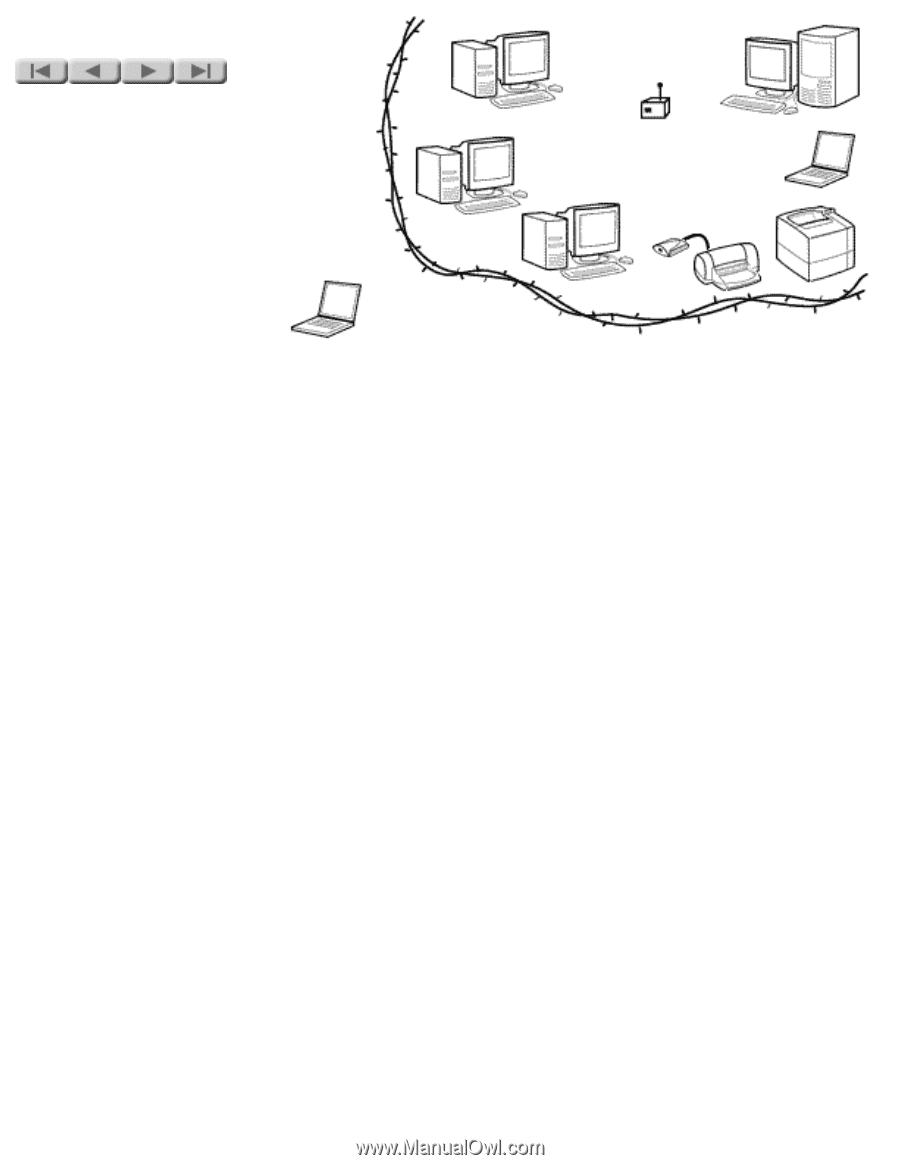
NETWORKS Wireless security Wireless networks are inherently less secure than wired ones. In a wired environment an intruder needs to gain physical access to your network wiring to break into your network; in a wireless environment, he just needs to be in range of the radio waves that carry the network traffic. Since these waves penetrate building walls and easily carry for tens of meters, an intruder sitting in a car in your parking lot could monitor the traffic on the wireless LAN in your building. To frustrate intruders, a number of standards have been developed to make security for a wireless network more-or-less equivalent to that of wired networks. These standards work in three areas: Network name (SSID): A network name, or service set identifier (SSID) is an alphanumeric character string that provides basic access control on a wireless network. To transmit onto the network, the network name of a computer or other device must match the name configured into the access point. Authentication: Authentication verifies the identity of a user or device before the user or device is allowed to transmit onto the network. There are several different schemes of authentication that you might encounter when installing an HP Jetdirect print server: q Open system: No authentication. q Shared key: Each device