ZyXEL ARMOR G1 User Guide - Page 128
IPv6 Firewall-Add Rule Screen, Settings, Firewall, IPv6 Firewall, Add Rule, LABEL, DESCRIPTION
 |
View all ZyXEL ARMOR G1 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 128 highlights
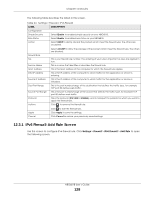
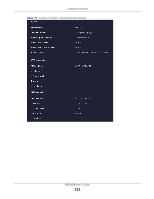
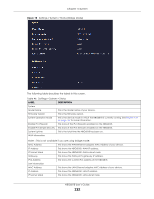
Chapter 12 Security The following table describes the labels in this screen. Table 44 Settings > Firewall > IPv6 Firewall LABEL DESCRIPTION Configuration Simple Security Rule Status Action Select Enable to enabled simple security on your NBG6818. Select Enable to enabled rule status on your NBG6818. Select DROP to silently discard the packets which meet the firewall rules. The others are accepted. Firewall Rule No. Service Name MAC Address Dest IP Address Source IP Address Dest Port Range Source Port Range Protocol Actions Select ACCEPT to allow the passage of the packets which meet the firewall rules. The others are blocked. This is your firewall rule number. The ordering of your rules is important as rules are applied in turn. This is a name that identifies or describes the firewall rule. This is the MAC address of the computer for which the firewall rule applies. This is the IP address of the computer to which traffic for the application or service is entering. This is the IP address of the computer to which traffic for the application or service is initialized. This is the port number/range of the destination that defines the traffic type, for example TCP port 80 defines web traffic. This is the port number/range of the source that defines the traffic type, for example TCP port 80 defines web traffic. This is the protocol (TCP, UDP or ICMPv6) used to transport the packets for which you want to apply the firewall rule. Click to remove the firewall rule. Apply Cancel Click to edit the firewall rule. Click Apply to save the settings. Click Cancel to restore your previously saved settings. 12.3.1 IPv6 Firewall-Add Rule Screen Use this screen to configure IPv4 firewall rule. Click Settings > Firewall > IPv6 Firewall > Add Rule to open the following screen. NBG6818 User's Guide 128