ZyXEL ARMOR G1 User Guide - Page 92
Port Trigger Screen
 |
View all ZyXEL ARMOR G1 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 92 highlights
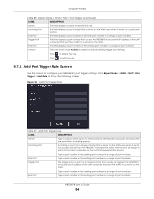
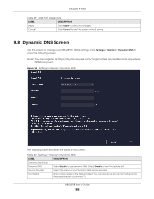
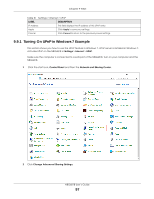
Chapter 9 WAN The following table describes the labels in this screen. Table 27 Settings > Internet > Passthrough LABEL DESCRIPTION ALG Setup FTP Select Enable to allow TCP packets with a specified port destination to pass through. H.323 Select Enable to allow peer-to-peer H.323 calls. SIP Select Enable to make sure SIP (VoIP) works correctly with port-forwarding and address- mapping rules. SNMP Select Enable to allow a manager station to manage and monitor the NBG6818 through the network via SNMP. RTSP Select Enable to have the NBG6818 detect RTSP traffic and help build RTSP sessions through its NAT. IRC Select Enable to allow clients to have real-time communications with others on the Internet. VPN Passthrough PPTP Select Enable to allow VPN clients to make outbound PPTP connections. It is required in order to connect to a PPTP VPN account. If PPTP is disabled, then when a client sends a request to a VPN server, the server will reply to the NBG6818 and the NBG6818 will drop the request. When PPTP is enabled, the NBG6818 will forward the reply from the VPN server to the client that initiated the request, and the connection will establish successfully. L2TP Select Enable to allow VPN clients to make outbound L2TP connections. It is required in order to connect to a L2TP VPN account. If L2TP is disabled, then when a client sends a request to a VPN server, the server will reply to the NBG6818 and the NBG6818 will drop the request. When L2TP is enabled, the NBG6818 will forward the reply from the VPN server to the client that initiated the request, and the connection will establish successfully. IPSEC Select Enable to allow VPN clients to make outbound IPSec connections. It is required in order to connect to a IPSec VPN account. If IPSEC is disabled, then when a client sends a request to a VPN server, the server will reply to the NBG6818 and the NBG6818 will drop the request. When IPSEC is enabled, the NBG6818 will forward the reply from the VPN server to the client that initiated the request, and the connection will establish successfully. Apply Click Apply to save your changes back to the NBG6818. Cancel Click Cancel to begin configuring this screen afresh. 9.7 Port Trigger Screen Some services use a dedicated range of ports on the client side and a dedicated range of ports on the server side. With regular port forwarding, you set a forwarding port in NAT to forward a service (coming in from the server on the WAN) to the IP address of a computer on the client side (LAN). The problem is that port forwarding only forwards a service to a single LAN IP address. In order to use the same service on a different LAN computer, you have to manually replace the LAN computer's IP address in the forwarding port with another LAN computer's IP address. Trigger port forwarding addresses this problem. Trigger port forwarding allows computers on the LAN to dynamically take turns using the service. The Zyxel Device records the IP address of a LAN computer that sends traffic to the WAN to request a service with a specific port number and protocol (a "trigger" port). When the Zyxel Device's WAN port receives a response with a specific port number and protocol ("open" port), the Zyxel Device forwards the traffic to the LAN IP address of the computer that sent the request. After that computer's connection for that service closes, another computer on the LAN can use the service in the same manner. This way you do not need to configure a new IP address each time you want a different LAN computer to use the application. NBG6818 User's Guide 92